One of the very first critical decisions that must be made when deciding to migrate to Office 365, considering which authentication model you want to lead off with is very crucial. Authentication is key to gaining access to any business critical system. Microsoft has given you many different ways of authenticating your environment with Office 365. In fact, there are some newer ways of authentication that can provide many benefits in terms of complexity and reducing the infrastructure footprint in the environment for authenticating Office 365 requests. Let’s take a look at choosing the right Office 365 authentication option pros and cons and see the various options available as you plan your migration to the Office 365 SaaS cloud.
Why Choosing the Right Office 365 Authentication Option is Important
Choosing the right Office 365 authentication option is very important as it affects many aspects of your deploy including where authentication takes place, how much on-premises infrastructure is needed to support the configuration, and also authentication behavior and options in times of disaster recovery.
There are four options for configuring Office 365 authentication to consider when architecting your Office 365 migration/authentication configuration. These are:
- Cloud only
- Directory sync with password hash
- Directory sync with pass through authentication
- Directory sync with Active Directory Federation Services
There are various factors to consider when choosing the right Office 365 authentication option, including the following:
- What experience do you want for your end users?
- What experience do you want for your admins?
- What kind of maintenance and operational effort can you handle?
- What are your security and compliance requirements?
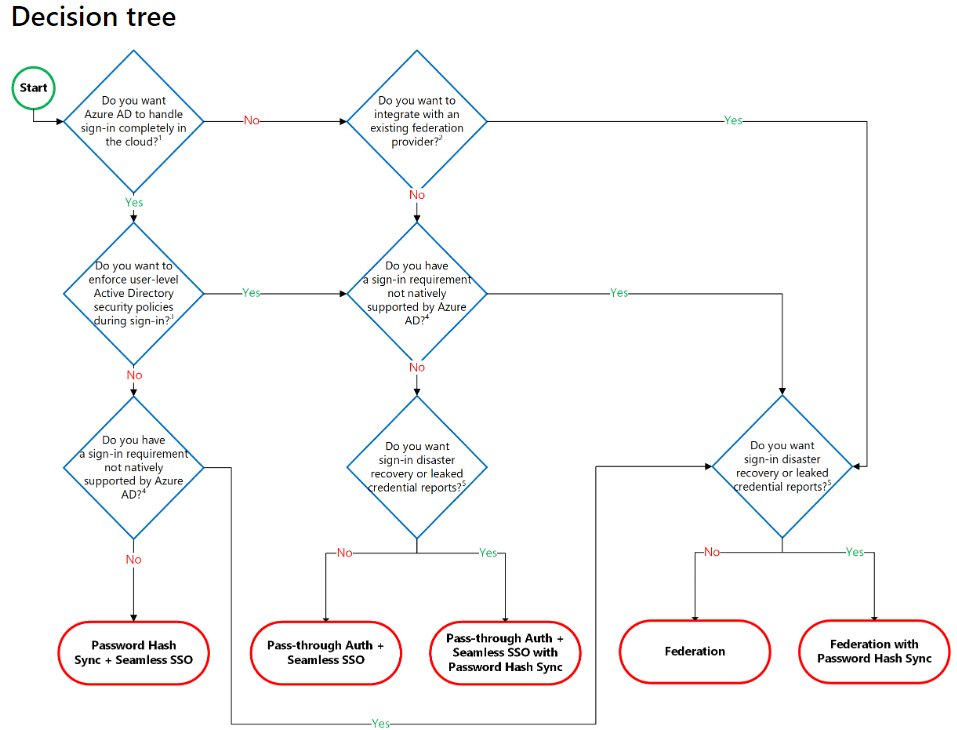
Microsoft has published a decision tree for helping to make the decision on which authentication provider may work best when choosing the right Office 365 authentication option.
Let’s take a look at each of these methods when choosing the right office 365 authentication option to see the pros and cons of each configuration and why you would choose one over the other.
Cloud only
When looking at choosing the right Office 365 authentication option, with the cloud only authentication method, user accounts are solely stored in Azure AD and no directory synchronization takes place from on-premises Active Directory Domain Services to the cloud.
Why would you use this method?
- It is easy, there is no synchronization mechanism that needs configured from the on-premises environment
- It is totally handled by Microsoft and you don’t have to worry about taking care of your logins
Why wouldn’t you use this method?
- You need to synchronize your on-premises directory with the cloud
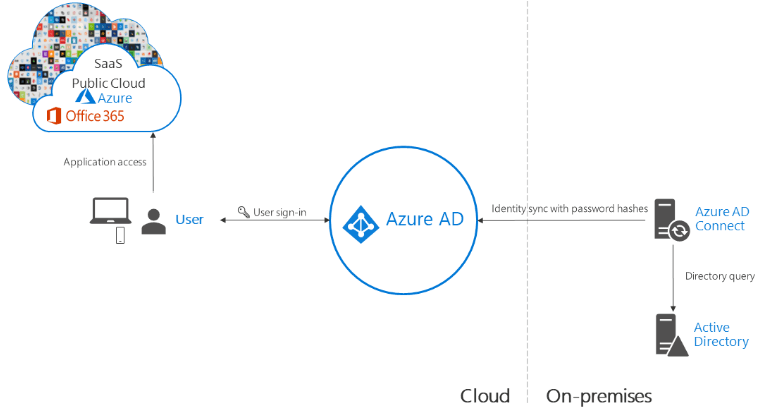
Directory Sync with Password Hash
The Directory Synchronization with Password Hash is one of the options that has been around for a while. It makes use of Azure AD Connect to synchronize on-premises Active Directory. This is the simplest of the directory synchronization configurations that can be deployed for synchronizing passwords to Azure AD which is the back end for Office 365.
Why would you use it?
- This is one of the simple deployment methods for synchronizing your on-premises Active Directory accounts to Azure AD
- You can also use it with Azure MFA to use multi-factor authentication
Why would you choose a different authentication option?
- Accounts that are disabled are not disabled immediately. There is a skew of some time before disabled accounts are synchronized with Azure AD
- Account logon restrictions from on-premises Active Directory are not synchronized with Azure AD Connect
- Multi-factor authentication from third-party vendors
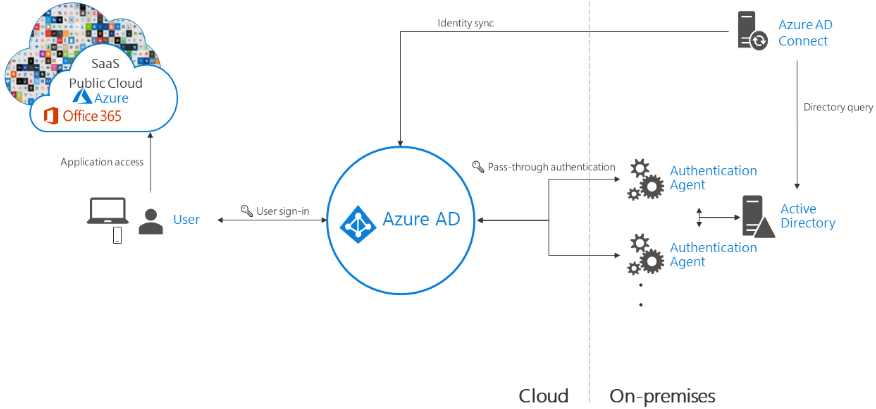
Directory Sync with Pass-Through Authentication
This is one of the newer directory sync mechanisms that provides enhanced features when compared to the password hash synchronization option. It is like a hybrid between password hash sync and the full-blown ADFS authentication option. With pass-through authentication, identities are synchronized between on-premises and Azure AD, however, the actual authentication request is passed back down to the on-premises environment for the authentication process. There are many advantages to using this mechanism and are similar to ADFS.
Why would you use it?
- You want to have more control over your authentication
- You own the authentication process instead of MSFT
- You need accounts to be disabled immediately
- Centralized logging that falls in line with what you are used to in your own on-premises environment
- You prefer a simpler infrastructure footprint when compared to full-blown ADFS
Why would you not use it?
- If you want to filter specific Office 365 services depending on client location
- You fully own authentication so high-availability of the solution depends on your infrastructure
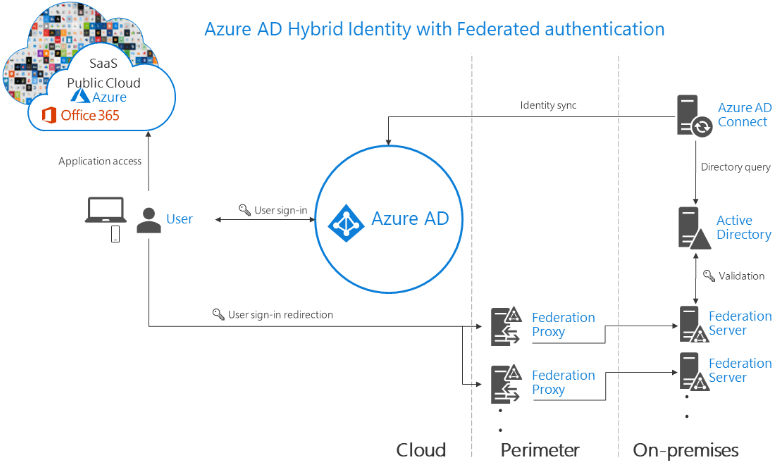
Directory sync with Active Directory Federation Services
When choosing the right Office 365 authentication option, Active Directory Federation Services or ADFS is the premier option for on-premises directory synchronization and features. ADFS offers great integration with Office 365 and Azure AD. Additionally, it allows you to own control of the authentication process.
Why would you use it?
- You want to have the ability to filter out specific Office 365 services based on client location
- You want to add branding or other customizations
- You want to configure domain joined single sign-on
- You want to have immediate account disablement and/or logon restrictions enforced
- Great third-party multi-factor authentication support
Why would you not choose this Office 365 authentication option?
- It can be complicated and complex to configure and architect correctly
- When ADFS goes down on-premises, no one can login to Office 365
Compliance Concerns Choosing the Right Office 365 Authentication Option
Not only do you have to think about the aspects of hybrid authentication in the areas of infrastructure footprint, capabilities of each hybrid authentication mechanism, and disaster recovery, you also need to think a bit about compliance concerns. Particularly in the area of log gathering and auditing, each authentication option has different capabilities when thinking about logging.
- ADFS – This method will allow having logging captured in the Windows event log
- Password hash sync – authentication logs will be stored in Azure and will need to be aggregated with other logs for compliance purposes if needed
- Pass-through authentication – the logs are in the event logs of the connector servers and will need to be aggregated
- Organizations can use both the Azure Active Directory Identity Protection and Azure AD Connect Health to help with some of the security monitoring concerns and checklists for compliance.
Wrapping Up – Choosing the Right Office 365 Authentication Option Pros and Cons
You would think it would be an easy choice in choosing the right Office 365 authentication option, however each has strengths and weaknesses to look at. Depending on the needs of your business as well as infrastructure footprint and complexity, these considerations may drive the decision one way or another. Other concerns such as disaster recovery and resiliency of authentication leads to more complexity for on-premises authentication and can help make the decision for choosing Microsoft to be the holder of teh “keys” for authentication requests. However, picking the right authentication option is key to having a successful migration or hybrid deployment with Office 365.
Google is updating how articles are shown. Don’t miss our leading home lab and tech content, written by humans, by setting Virtualization Howto as a preferred source.