VMware patches new Intel speculative execution microarchitectural data sampling MDS vulnerability
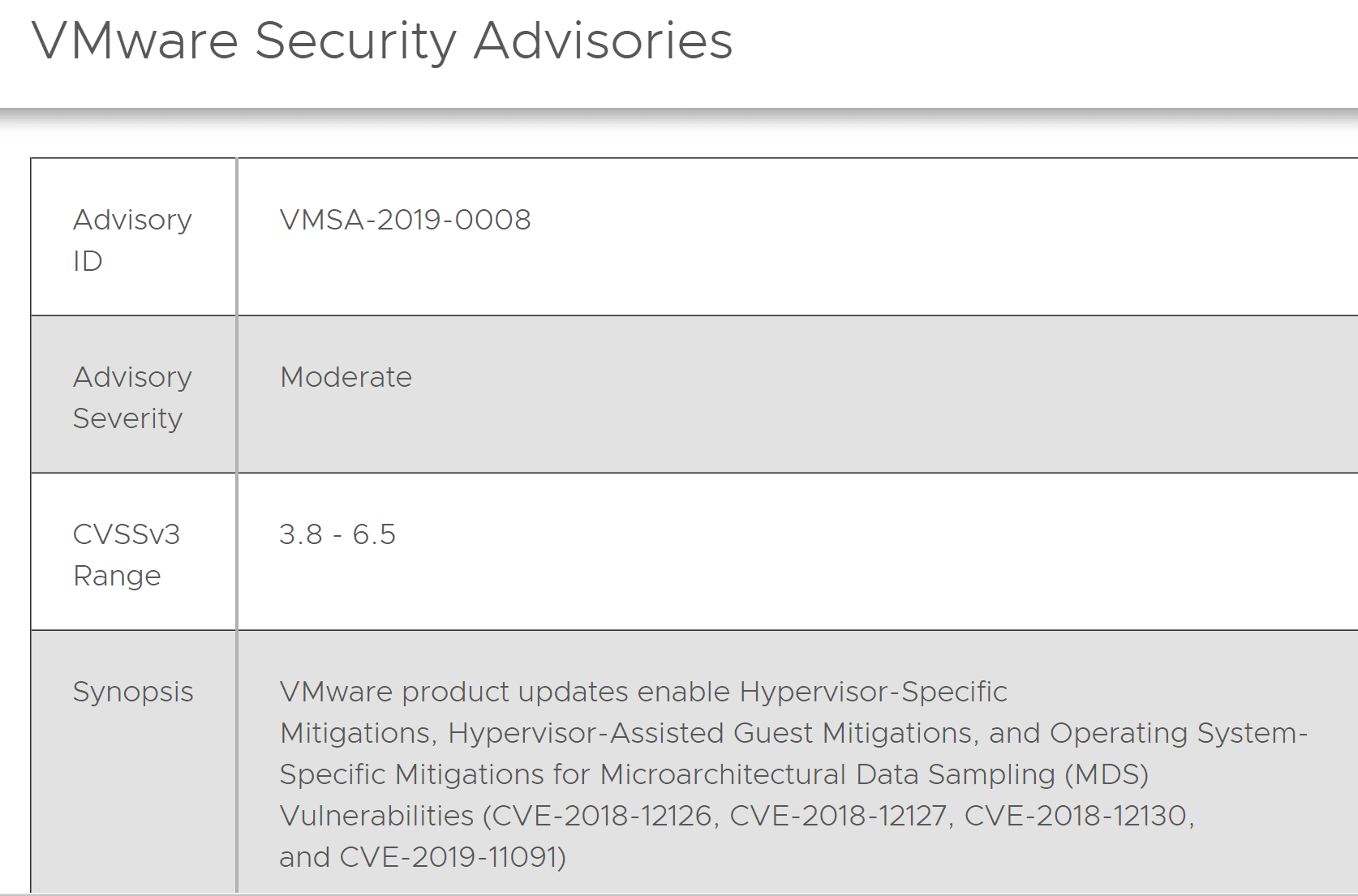
Perhaps the biggest security news of 2018 was the CPU flaws discovered with speculative execution vulnerabilities in Intel CPUs specifically and also AMD flaws discovered as well. Over a year later now we have news of a new speculative execution vulnerability discovered by security researchers. The new speculative execution vulnerability is known as Microarchitectural Data Sampling (MDS). This is a new very concerning security flaw announced by Intel and security researchers that details that an attacker can have access to any stream of data that the Intel CPU touches. VMware announced a new security advisory yesterday at the time of this writing detailing security patches to help mitigate this new concerning attack. In this post we will take a look at VMware patches new Intel speculative execution microarchitectural data sampling MDS vulnerability. Let’s take a closer look at what the MDS vulnerability is and the VMware specific patch implications.
What is the
Microarchitectural Data Sampling (MDS) Vulnerability?
In certain conditions, data that exists in microarchitectural structures may be speculatively accessed by faulting or assisting load or store operations that currently running software does not have permissions to access. Software may be able to send this speculatively accessed data to a side channel disclosure capturing mechanism that could allow malicious threat actors to infer data.
According to Intel, this exploit can occur on Intel microarchitecture prior to 2nd Generation Intel® Xeon® Scalable Processors (formerly known as Cascade Lake). These issues may allow a malicious user who can locally execute code on a system to infer data otherwise protected by architectural mechanisms.
Microarchitecture Data Sampling involes the following:
Microarchitectural Store Buffer Data Sampling (MSBDS) CVE-2018-12126
Microarchitectural Fill Buffer Data Sampling (MFBDS) CVE-2018-12130
Microarchitectural Load Port Data Sampling (MLPDS) CVE-2018-12127
Microarchitectural Data Sampling Uncacheable Memory (MDSUM) CVE-2019-11091
VMware patches new Intel speculative execution microarchitectural data sampling MDS vulnerability
Relative to VMware products, VMware has identified the following products as being vulnerable to the new attack vector using MDS:
- VMware vSphere ESXi (ESXi)
- VMware Workstation Pro / Player (WS)
- VMware Fusion Pro / Fusion (Fusion)
- vCloud Usage Meter (UM)
- Identity Manager (vIDM)
- vCenter Server (vCSA)
- vSphere Data Protection (VDP)
- vSphere Integrated Containers (VIC)
- vRealize Automation (vRA)
VMware has identified the following attack vectors with VMware products:
A malicious user must have local access to a virtual machine and the ability to execute code to infer data otherwise protected by architectural mechanisms from another virtual machine or the hypervisor itself via MDS vulnerabilities.
With operating system specific MDS vulnerabilities, a malicious user must have local access to a virtual machine and the ability to execute code to infer data otherwise protected by architectural mechanisms within the Guest Operating System (Intra-VM) via MDS vulnerabilities.
There are two known attack vector variants for MDS at the Hypervisor level:
- Sequential-context attack vector (Inter-VM): a malicious VM can potentially infer recently accessed data of a previous context (hypervisor thread or other VM thread) on either logical processor of a processor core.
- Concurrent-context attack vector (Inter-VM): a malicious VM can potentially infer recently accessed data of a concurrently executing context (hypervisor thread or other VM thread) on the other logical processor of the Hyper-Threading-enabled processor core.
VMware MDS Vulnerability Mitigations
What resolutions are available for the VMware products listed above?
- The first resolution relates to the sequential-context attack vector for Inter-VM attack vector – The resolution is a hypervisor update to the latest version of the hypervisor that is noted in the table below. The Intel microcode updates need to be in place which can be implemented by previously released ESXi patches. It is noted there is not a significant performance impact.
- The concurrent-context attack vector or Inter-VM exploit is enabled by the ESXi side-channel scheduler version 1 or version 2. It is noted there is not a significant performance impact due to the side-channel patch.
The following table is from VMware showing the fixed version of each VMware product with the appropriate mitigation implemented.
| Product | Version | Running On | CVE Identifier | CVSSv3 | Severity | Fixed Version | Workarounds | Additional Documentation |
| vCenter Server1 | 6.7 | Any | N/A | N/A | N/A | 6.7 U2a | None | KB67577 |
| vCenter Server1 | 6.5 | Any | N/A | N/A | N/A | 6.5 U2g | None | KB67577 |
| vCenter Server1 | 6.0 | Any | N/A | N/A | N/A | 6.0 U3i | None | KB67577 |
| ESXi | 6.7 | Any | CVE-2018-12126 CVE-2018-12127 CVE-2018-12130 CVE-2019-11091 | 6.5 | Moderate | ESXi670-201905401-BG ESXi670-201905402-BG2 ESXi670-201905403-BG | None | KB67577 |
| ESXi | 6.5 | Any | CVE-2018-12126 CVE-2018-12127 CVE-2018-12130 CVE-2019-11091 | 6.5 | Moderate | ESXi650-201905401-BG ESXi650-201905402-BG2 | None | KB67577 |
| ESXi | 6.0 | Any | CVE-2018-12126 CVE-2018-12127 CVE-2018-12130 CVE-2019-11091 | 6.5 | Moderate | ESXi600-201905401-BG ESXi600-201905402-BG2 | None | KB67577 |
| Workstation | 15.x | Any | CVE-2018-12126 CVE-2018-12127 CVE-2018-12130 CVE-2019-11091 | 6.5 | Moderate | 15.1.0 | None | KB68025 |
| Fusion | 11.x | Any | CVE-2018-12126 CVE-2018-12127 CVE-2018-12130 CVE-2019-11091 | 6.5 | Moderate | 11.1.0 | None | KB68025 |
Wrapping Up
This is yet more fall out from the speculative execution vulnerabilities found in Intel processors. Looking at the news that VMware patches new Intel speculative execution microarchitectural data sampling MDS vulnerability, we can see this is yet another iteration of the design flaws from a security standpoint of Intel processors prior to Cascade Lake. Organizations will want to take a look at their current patch levels and implement the latest patches outlined in the VMware security advisory 2019-0008. No doubt there may be other advisories to come with new vulnerabilities as they are found and patched.