Use PowerShell to Create Palo Alto EDL for Dynamic DNS Clients
One of the really cool things you can do with the Palo Alto firewall is create external dynamic lists which allow dynamically aggregating a number of different resource types to allow the Palo Alto firewall to dynamically act on the objects in the list to apply policy, etc. As I have covered in the past, there is a really great solution that was brought forth by Palo Alto and open sourced called Minemeld. With Minemeld you can aggregate a number of different EDL resources and present these to the Palo Alto. However, recently, I had a quick use case in conjuntion with dynamic dns hosts to allow applying policy to allow dynamic dns hostnames to be able to connect to a Palo Alto firewall. I wasn’t able to quickly figure out an easy way to do this in Minemeld (as I am sure it can be). However, expendiancy often breeds solutions at the spur of the moment. I was able to instead use a simple PowerShell script to poll a couple of dynamic DNS names and create a text file that I could host on an internal web server to feed a Palo Alto EDL. In this post, we will take a look at how to Use PowerShell to Create Palo Alto EDL for Dynamic DNS clients.
What are Palo Alto External Dynamic Lists or EDLs?
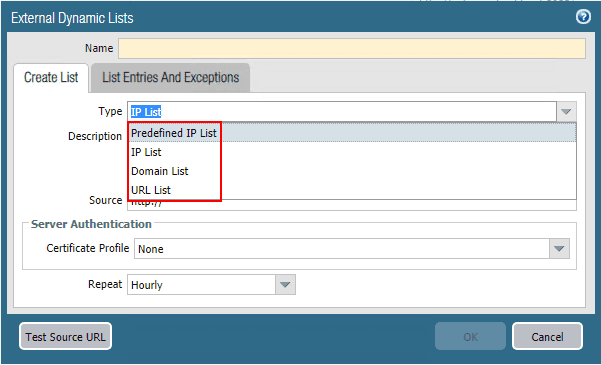
External Dynamic Lists or EDLs are text files hosted on a web server that allows a Palo Alto firewall to connect to to dynamically import objects, including IP addresses, URLs, and domains. These can then be used in policy enforcement, either in a positive or negative sense. The advantage of the EDLs is they are dynamic. This means that objects in the EDL can change, and you don’t have to go in and manually update policies as they are configured with the EDL, they change automatically. There are four types of EDL objects:
- IP Address – can contain single IP addresses, IP addresses with subnet, or IP ranges
- Predefined IP Address – A predefined IP list that refers to any of the two Palo Alto Networks Malicious IP Address Feeds.
- URL – An EDL containing URLs that have been deemed to be malicious or dropping malware payloads
- Domain – An EDL containing domain names to enforce policy using anti-spyware profiles.
Why Use an EDL instead of FQDN Object?
One thing I don’t like about Palo alto FQDN objects is the frequency of which they are updated. According to the official Palo Alto documentation at the time of this writing (if I haven’t missed something obvious here), the default refresh interval for FQDN objects is 30 minutes. However, starting in PAN-OS 6.1, you can now configure this interval down to 10 minutes.
So, painting a scenario here, if you have a policy that is restricting access to only hosts that are found in FQDN address objects, if you have a change to the IP address of the FQDN object and your DDNS service has correctly updated this value, you would have to wait an entire 30 minutes before the firewall recognizes the change and properly updates the policy.
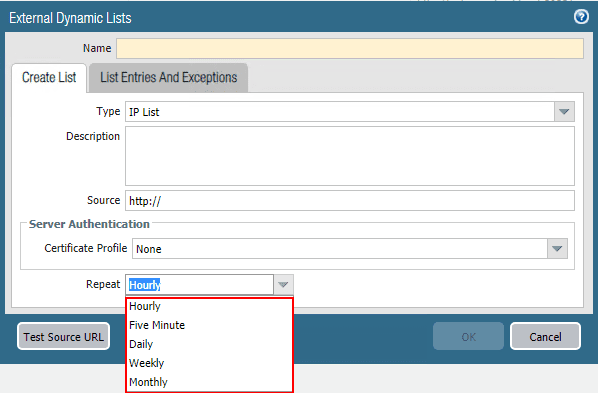
If you are like me, you may not have 30 minutes to wait on a refresh interval of 30 minutes to pass. The now-configurable 10 minute interval is much more desirable, however, a lower value of 5 minutes or less would be even better. In steps the EDL. With EDLs, as shown in the screen clip, I can have those refresh every 5 minutes. So, if I base policy off an EDL rather than an FQDN object, I will have much better convergence time from DDNS update to policy update on the firewall.
For my specific use case, I had only 2 addresses that I wanted to be updated in the EDL for policy purposes. I had Googled a bit on how to create a custom list for this with Minemeld but wasn’t able to come up with anything that worked right. I decided to create a list using PowerShell. Let’s see how.
Use PowerShell to Create Palo Alto EDL for Dynamic DNS clients
Please keep in mind, this is in no way, extremely slick PowerShell code here, very crude, but wanted to get something up and running very quickly. The outline of the workflow is as follows:
- Use a Windows Server running a webserver (already had this running)
- Flush DNS cache every minute
- Run a PowerShell snippet to do a DNS to IP lookup
- Write this to a text file formatted properly for consumption on the Palo Alto firewall
In a hurry, I came up with the following:
ipconfig /flushdns
$ddns1 = [System.Net.Dns]::GetHostAddresses("<your ddns FQDN 1") | Select -expandproperty IPAddressToString
set-content -path c:inetpubddnscheckddns.txt -value "$ddns1`r"
$ddns2 = [System.Net.Dns]::GetHostAddresses("<your ddns FQDN 2") | Select -expandproperty IPAddressToString
add-content -path c:inetpubddnscheckddns.txt -value "$ddns2`r`n"
The code is fairly self-explanatory. However, first I am flushing DNS cache to ensure the latest and greatest resolution is pulled. Next, using PowerShell to actually resolve the DNS name to an IP. Then expanding the property out to leave only the IP address itself in the return. Finally, the first pull is overwriting whatever is in the file with the set-content cmdlet. Then the next pull is adding to the text file with the second DDNS FQDN. If you notice the trailing tilde “r” and then tilde “n” (having to spell this out due to WordPress), this is used to introduce the proper carriage return needed. Just need the return for a new line on the first one, and then new line and carriage return on the second IP.
I had successfully created the file without it to begin with, but the Palo didn’t like the formatting and was giving me invalid IP from the list. After adding the new line and carriage return, however, this solved the issue and the EDL was successfully able to import the objects from this list.
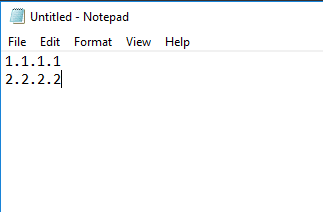
This creates a simple text file as follows:
The last piece of the puzzle was to simply create a scheduled task to run a batch file to run the PowerShell code which updated the text file served up by IIS. Batch file contents:
“C:WindowsSystem32WindowsPowerShellv1.0powershell.exe” -command ./yourpowershellcode.ps1
I set the batch file to run every minute which gives me good coverage and resolution to ensure the file is constantly updated. In this way, I have much better convergence on my Palo Alto. Instead of waiting 10 or even 30 minutes for FQDN objects to be updated, with the EDL I have this happening every 5 minutes pulling from a Windows text file served out and updated every minute.
Wrapping Up
As stated above, this is a very simple and crude example of what can be done with PowerShell and creating a basic EDL. However, it did what I needed it to do in a pinch. Hopefully this example of how to Use PowerShell to Create Palo Alto EDL for Dynamic DNS Clients will help anyone else needing to create a properly formatted EDL list for consuming in PAN-OS for having much faster convergence time on DDNS objects.







