Create DNS Sinkhole to Block Malware Domains with PAN-OS 9.0
This week Palo Alto released PAN-OS 9.0. There are over 60 new capabilities in this release of the new firmware and many great new features. There is a new security functionality introduced as part of PAN-OS 9.0 that is an integrated DNS security service that provides DNS sinkhole functionality for blocking traffic destined for malicous domains. This is a great new features that provides upgraded security capabilities for the already powerful PAN-OS and Palo Alto firewalls in general. In this post, we will take a look at how to create DNS Sinkhole to block malware domains with PAN-OS 9.0 and how this is configured.
What is a DNS Sinkhole?
What is a DNS sinkhole? A DNS sinkhole can be used on both sides of the fence for the bad guys as well as good guys. However, with PAN-OS 9.0, DNS sinkhole functionality is used for helping to disrupt attacks that use DNS for command and control (C2) or data theft. The tight integration with the Palo Alto features gives you automated protections and eliminates the need for stand-alone tools.
When you think about the importance of DNS, it integral to network communication today. It is what makes Internet communication possible without the need to memorize millions of IP addresses. However, as great as DNS is and the service it provides, there are certainly security vulnerabilities that can come up when thinking about what a compromised DNS server or name resolution theft can lead to.
Create DNS Sinkhole to Block Malware Domains with PAN-OS 9.0
Attacks based on DNS often are successful due to the lack of visibility by security teams into their organization’s DNS infrastructure and how threats might be using DNS to maintain control over infected devices. There are tools out there for providing visibility into this, however, they are often uncoordinated and may even require changes in the DNS infrastructure to work.
Based on Palo Alto’s own security team’s research some 80 percent of malware uses DNS to initiate the C2 operations. The number of DNS domains that are used for malicious purposes is mind boggling and is impossible to keep up with via manual methods. Additionally, more advanced threat tactics use DNS tunneling for data theft. DNS tunneling is a method attackers use to encode malicious payloads into DNS queries and responses. It can also be used in conjunction with a compromised DNS server to control a remote server/applications.
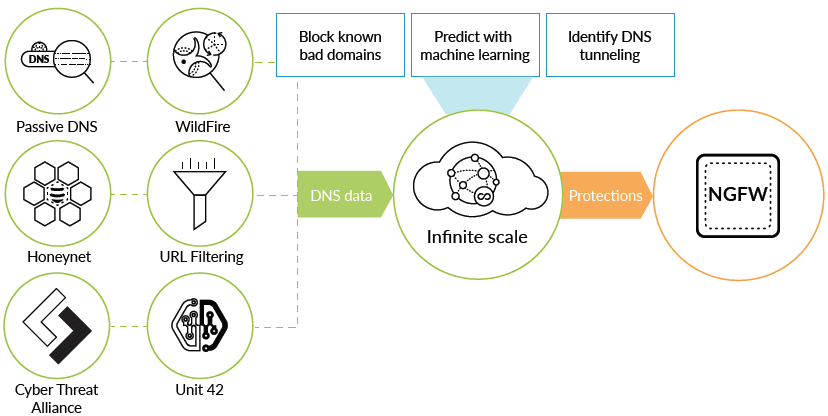
With the Palo Alto DNS Security service threats hidden in DNS traffic are identified with shared threat intelligence and machine learning. The firewall can then forward any traffic that is resolved to known or recently identified malware domains to a sinkhole that safely stops the traffic from proceeding.
Using the new Palo Alto DNS Security service allows predicting and blocking malicious domains, helping to give the advantage back to the network defenders. This new service allows the Palo Alto next-gen firewalls to:
- Provide automatic protection against tens of millions of malicious domains with real-time analysis and continuously gorwing, global threat intelligence.
- Predict and stop malicious domains from domain generation algorithm-based malware with instant enforcement. This utilizes machine learning to detect new and never-before-seen DGA domains by analyzing DNS queries.
- Provides limitless protection against malicious domains with a cloud-based database. Protections are always up-to-date.
- No performance impact is realized due to the service being hosted on Palo Alto’s global security service delivery network to provide low latency and high performance DNS protection
Examples of DNS tunneling malware:
- ALMA Communicator Trojan, which uses DNS tunneling to receive commands from the adversary and exfiltrate data. The malware employs specially crafted subdomains to send data to the C2 server and specific IPv4 addresses to transmit data from the C2 to the Trojan over DNS requests.
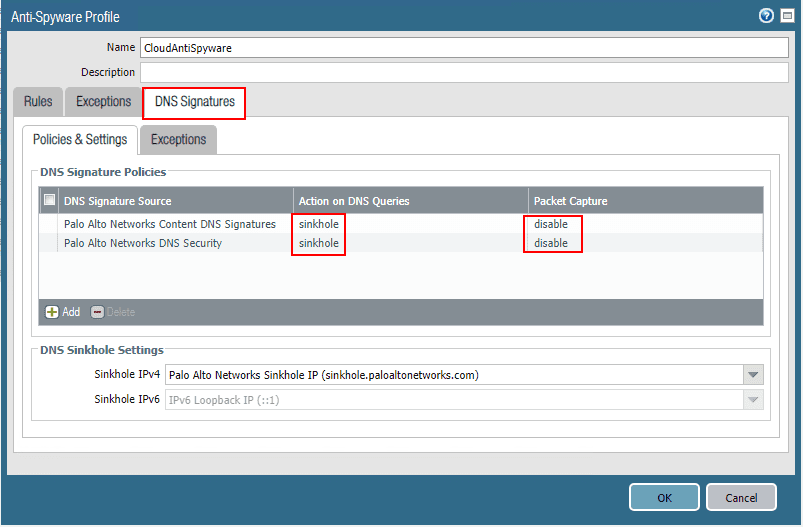
The new service is “free” for those that already have a paid subscription for a Threat Protection license. All you have to do is update your Palo Alto firewall to version 9.0 of PAN-OS to have access to the new feature. How is this configured? Navigate to Objects >> Security Profiles >> Anti-Spyware and clone either the default or strict profiles there by default. These are read-only so you will need to clone to make changes or at least that is what I am seeing.
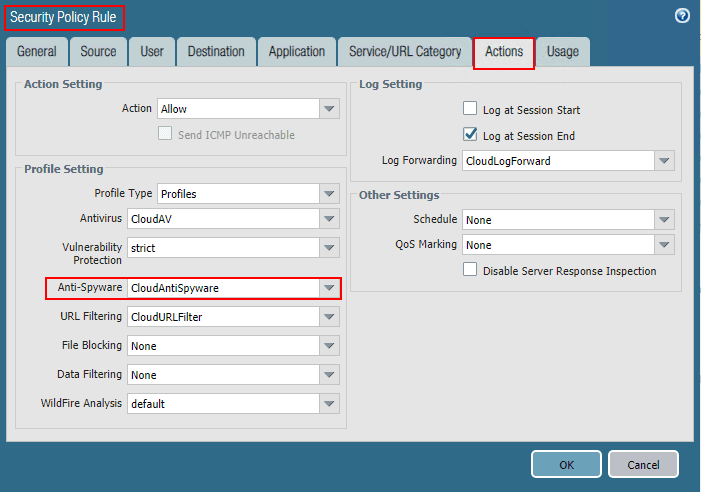
As simple as that, once you have the Anti-spyware object updated, and then have a security policy referencing the new DNS sinkhole-enabled policy, you can then take advantage of the DNS sinkhole functionality offered by the new PAN-OS 9.0 release.
Wrapping Up
This is great new functionality added to the Palo Alto next-gen firewall feature set. DNS is certainly a threat vector that can be difficult to secure and have visibility into. I like that the Palo Alto DNS security solution is part of the other next-gen firewall features and is as easy as a few check boxes and drop down menus to configure and enable. By securing DNS and filtering known malware domains, this provides a powerful means to prevent malicious payloads from being dropped to unsuspecting end users.