Installing New Windows 10 Sandbox Feature Networking Resources Browsers Security
One of the most intriguing new features in recent Windows 10 Insider Preview Builds for me personally has been the introduction of the new Windows Sandbox feature that allows having a totally isolated environment that allows for safely testing executables and other potentially dangerous file types before executing on the host machine. In downloading and playing around with the latest Windows Insider Preview Build 18317 release, I wanted to take a deeper dive into the new Windows 10 sandbox feature, taking a look at networking, users, security, etc. Let’s look at Installing New Windows 10 Sandbox Feature Networking Resources Browsers Security.
New Windows 10 Sandbox Feature
The new Windows 10 Sandbox Feature hopes to solve many of the longstanding issues with keeping a workstation free from unwanted or malicious executables and file types and being able to safely “detonate” these in a walled off area away from the host machine.
Typically, many solve this issue by having a “browsing VM” that is used to browse the Internet with an underprivileged account, execute potentially dangerous files and such. A snapshot can be taken of the workstation at the beginning of the day and then rolled back as needed to return this browsing VM back to a pristine state. This ensures you have no malware or unwanted code running on the machine.
The problem with this is that it is not very efficient. You have to run a hypervisor, install a full copy of Windows running in a virtual machine, license, etc. The resources required to run a full copy of Windows 10 in a virtual machine is certainly not insignificant.
The new Windows 10 Sandbox Feature melds together Hyper-V and container technology to create an isolated Windows 10 environment that utilizes files from the host operating system so that these are not reproduced or duplicated. The sandbox then runs a snapshot of sorts that is only used during the working session. Once the Windows sandbox application is closed, these changes are discarded.
Installing New Windows 10 Sandbox Feature Networking Resources Browsers Security
Let’s take a look at the process to get the Windows 10 Sandbox feature installed and how it is accessed. The installation or enabling of the Windows Sandbox is a simple process. Open Programs and Features or get there by typing appwiz.cpl and you will see the Windows Sandbox feature ready for/to installation/enable. ***Note*** if you don’t have virtualization features in your CPU you will see this greyed out. Additionally, like me, if you are running this inside a VM without the “nested virtualization” functionality/CPU features exposed to the guest, it will also be greyed out.
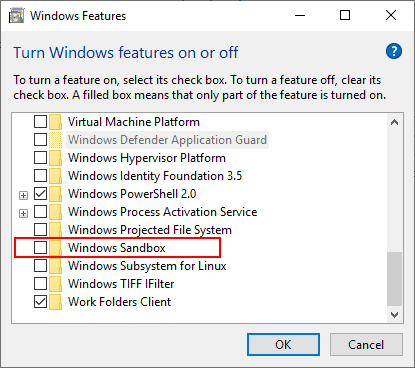
After enabling, you will see the prompt to restart Windows.
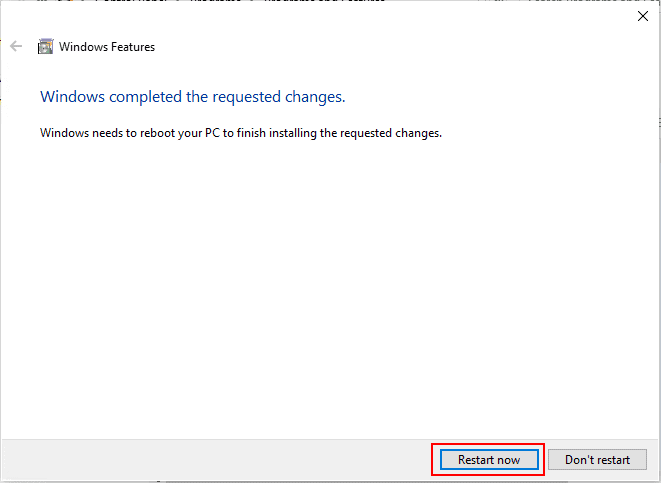
The feature will be configured on the restart.
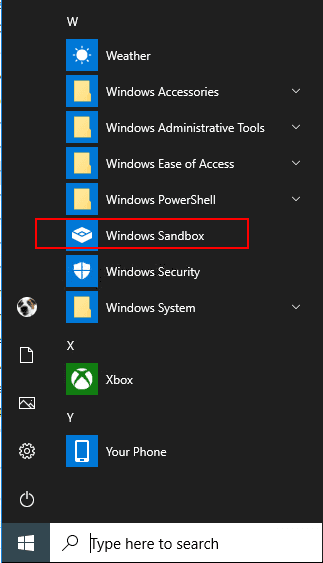
After rebooting and signing in, you can launch the Windows Sandbox from the Start menu.
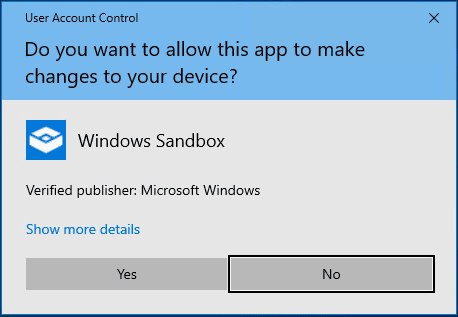
You will see a security prompt once you launch the app. Click Yes to verify.
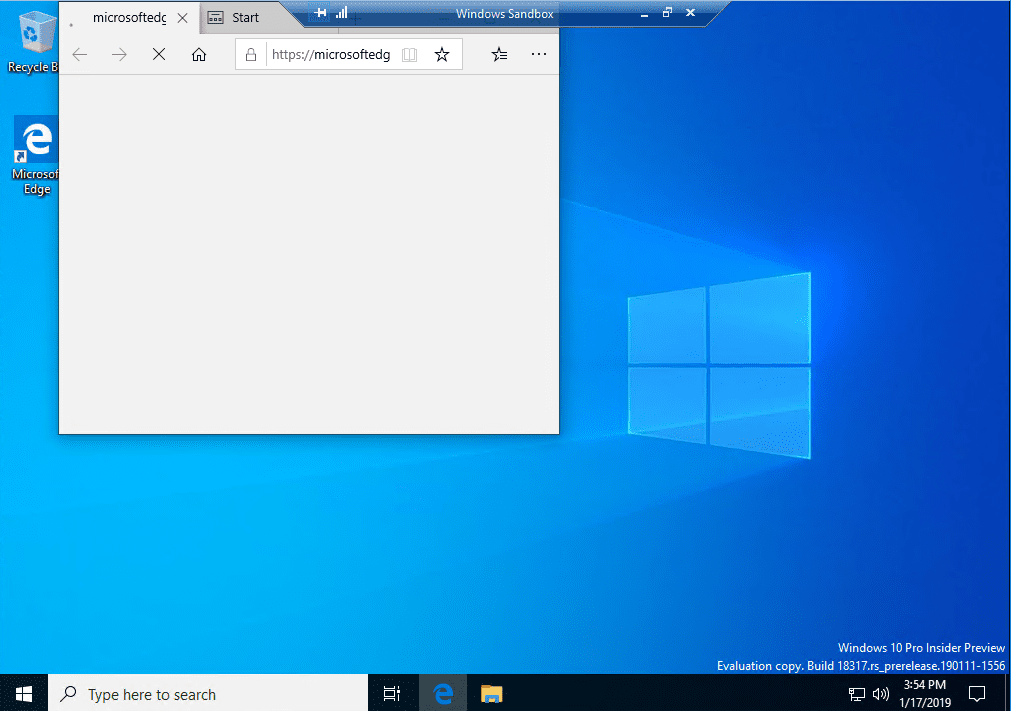
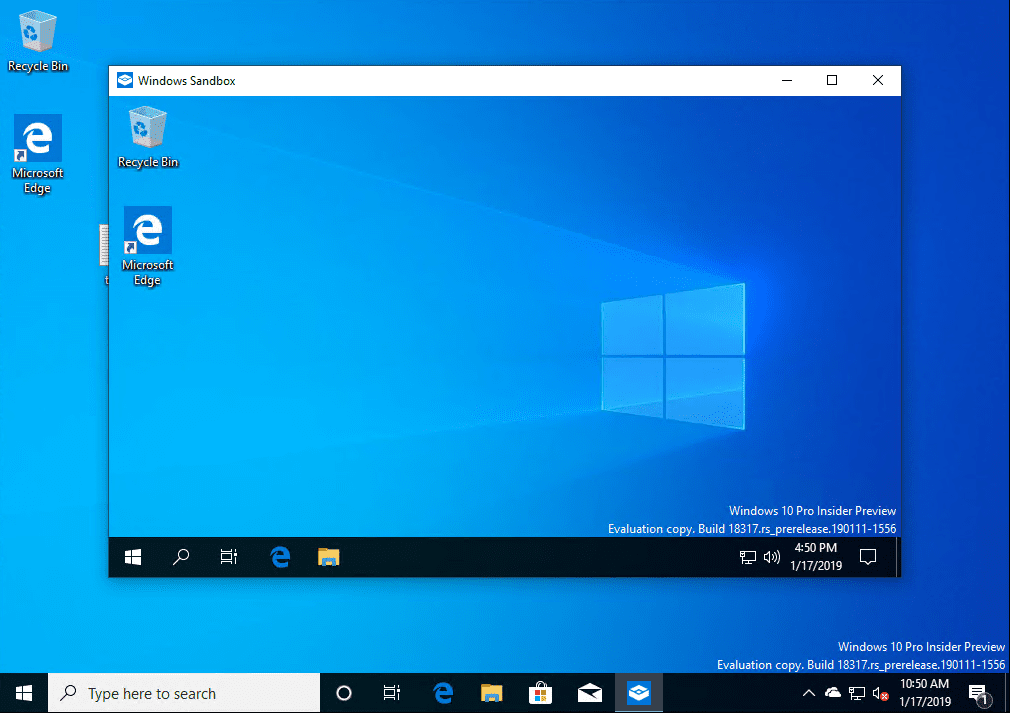
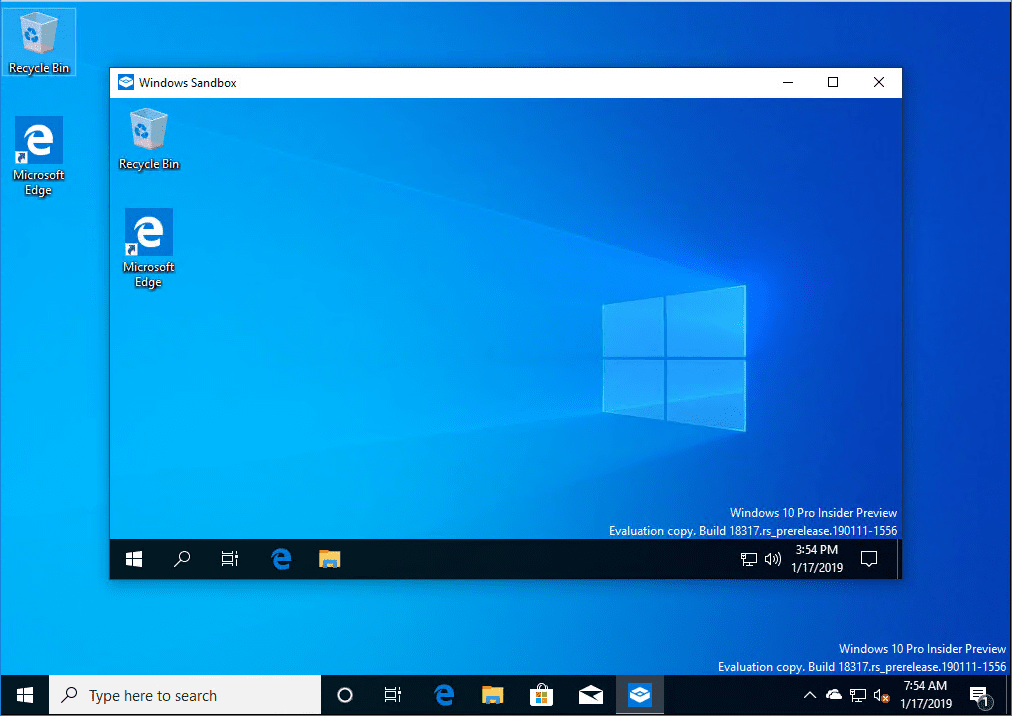
The Windows 10 Sandbox Windows app launches.
As you can see below, the new Windows 10 Sandbox looks like a VM running, or another instance of Windows running.
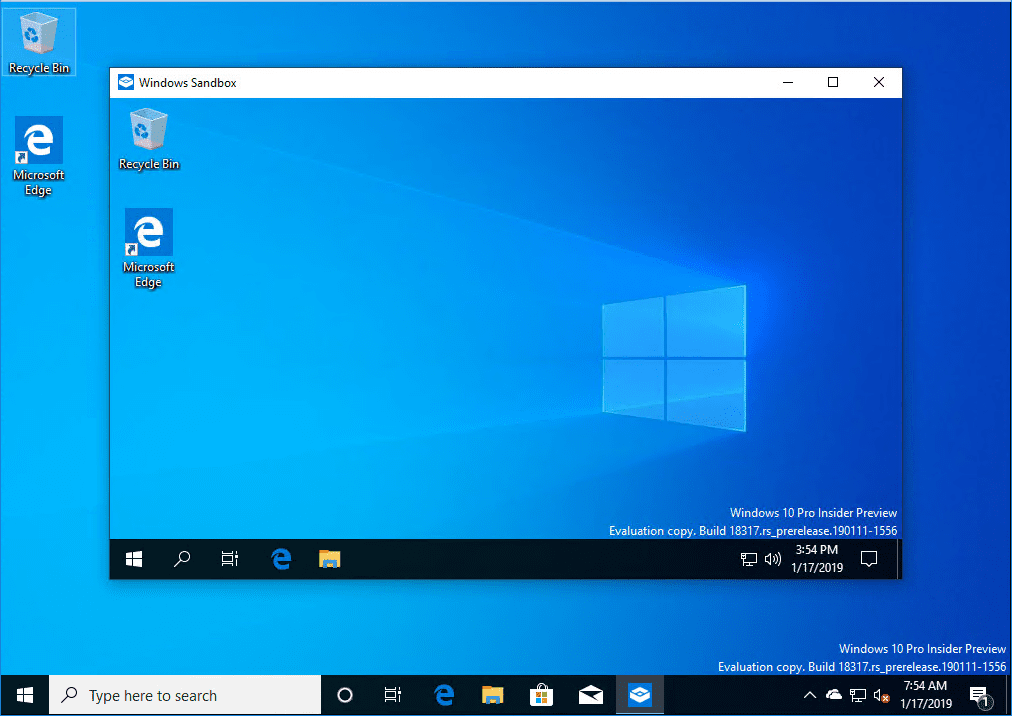
Maximizing the window looks like the Hyper-V virtual machine connection console.
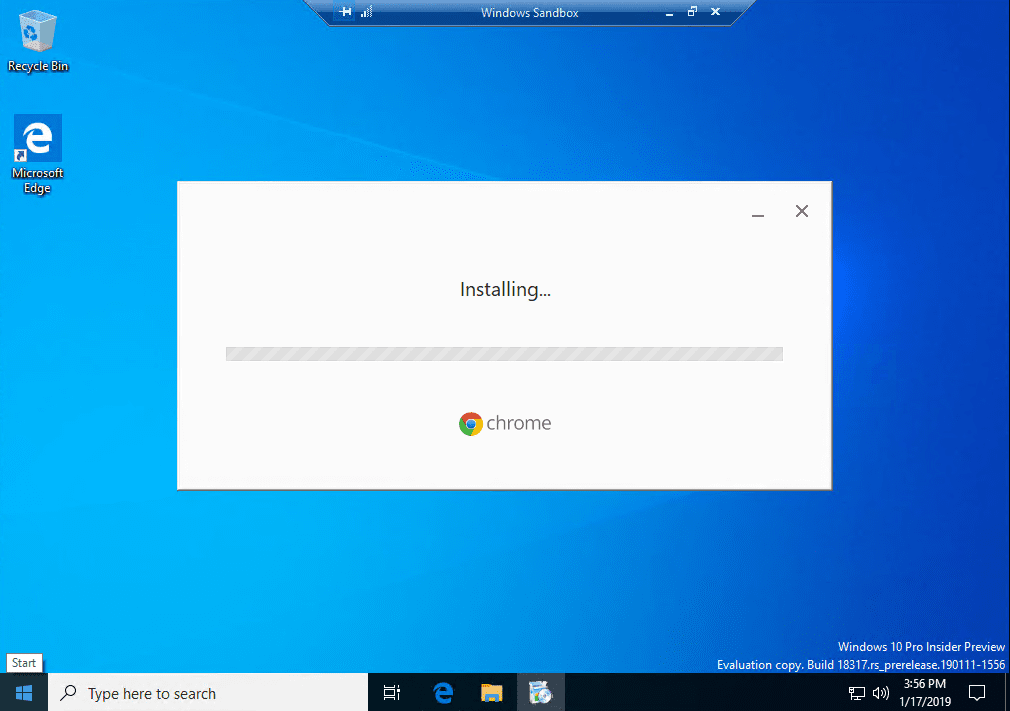
You may wonder, can you install Chrome and other apps? Yes you can as you can see below!
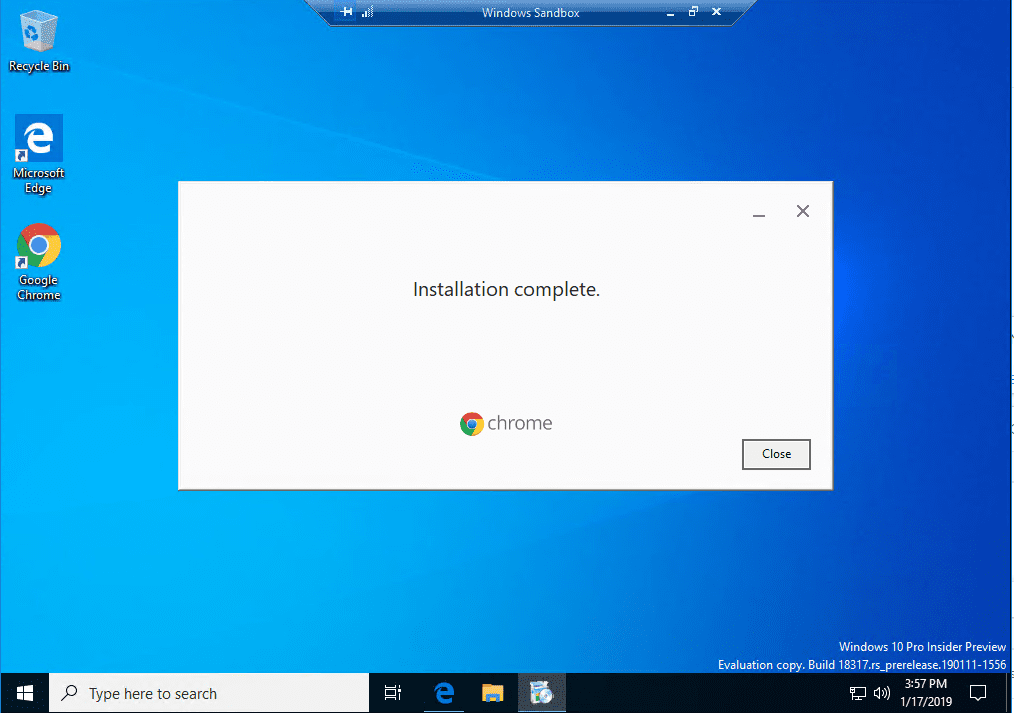
Chrome installation completes successfully.
You can see the isolation from the Windows 10 Sandbox and the host operating system. Chrome is installed in the Windows 10 Sandbox, but not in the host Windows 10 operating system.
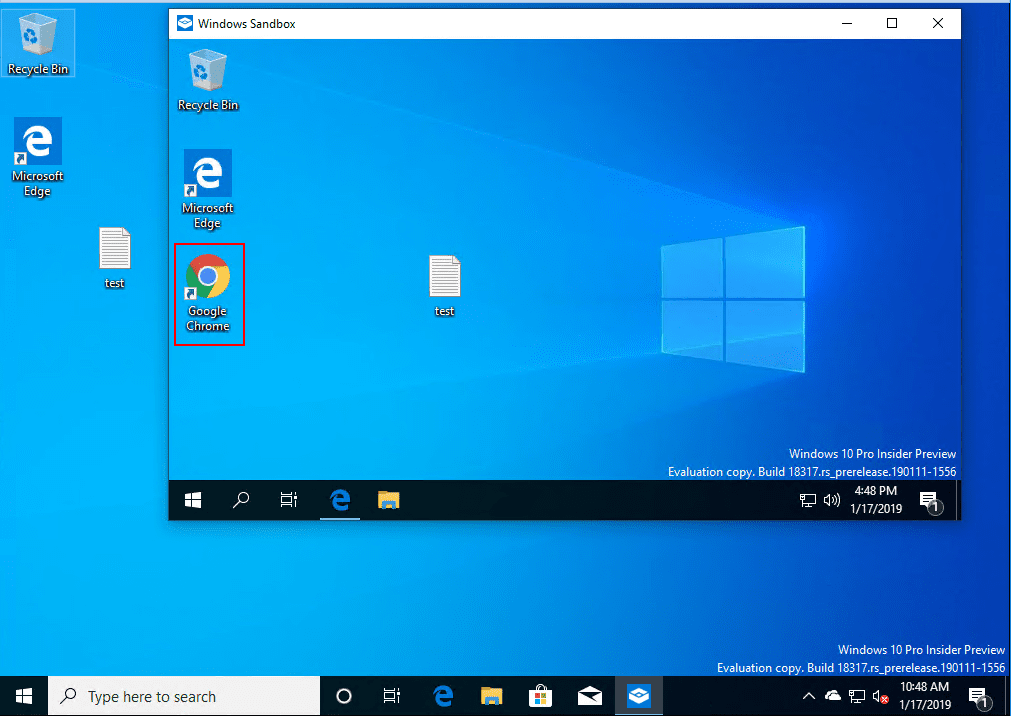
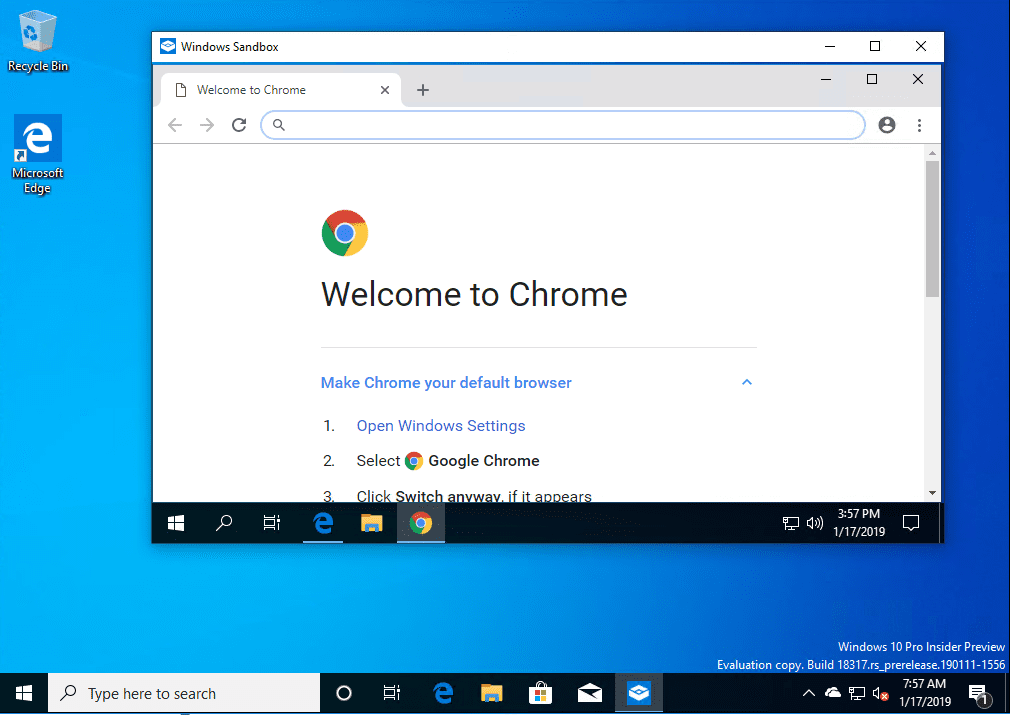
Chrome launched in the Windows 10 Sandbox.
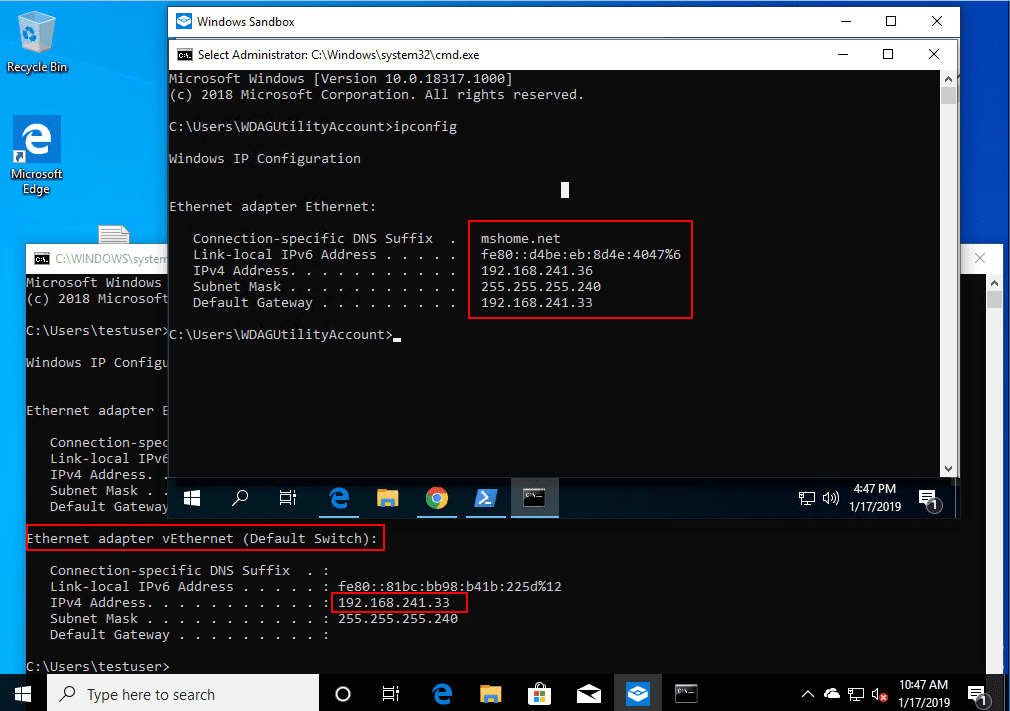
What about the networking configuration? I was curious how this was configured in the Windows 10 Sandbox app. It is a NAT’ed IP that has as its gateway the host Windows 10 OS that now has a vEthernet (Default Switch) installed and configured.
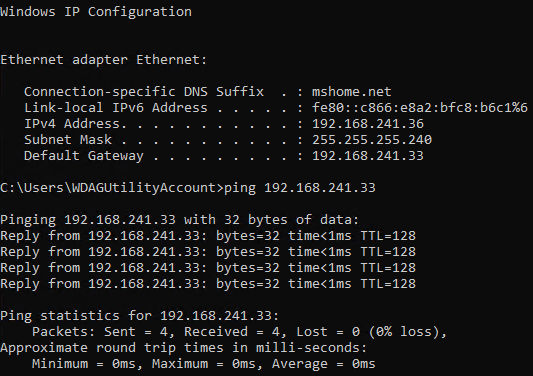
You can see the NAT’ed IP address with a .240 subnet. The gateway is the IP bound to the vEthernet adapter on the host.
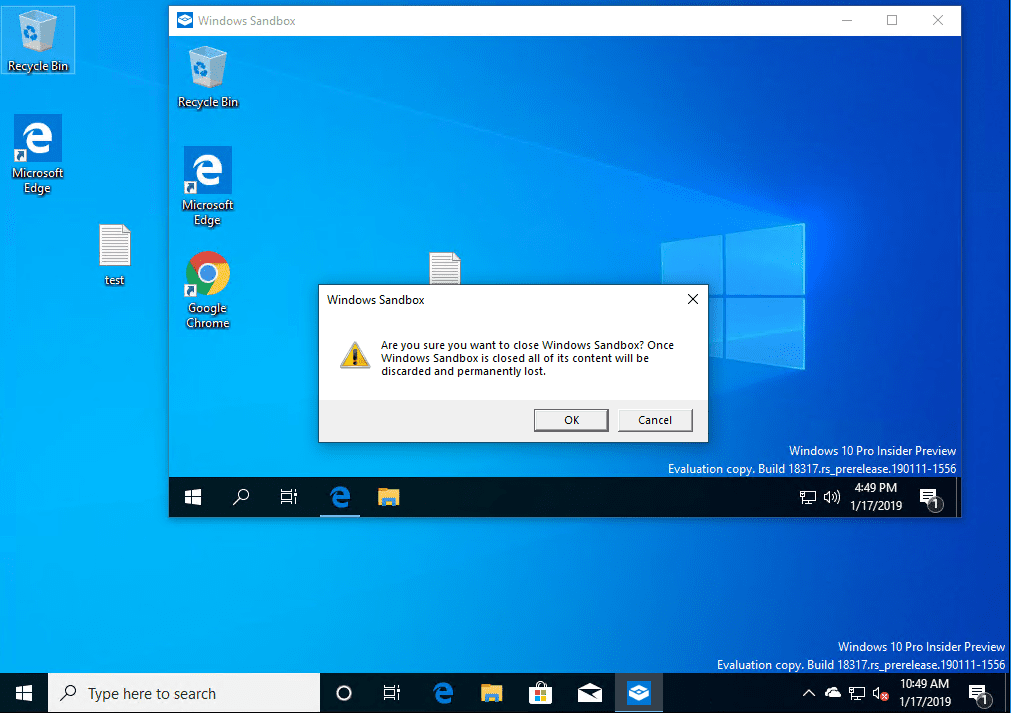
When you attempt to close the new Windows 10 Sandbox app, you will see a warning prompting you “are you sure you want to close Windows Sandbox? Once Windows Sandbox is closed all of its content will be discarded and permanently lost.” So the changes you make do not persist in the Windows 10 Sandbox environment.
Sure enough, after a relaunch, we no longer see Chrome installed.
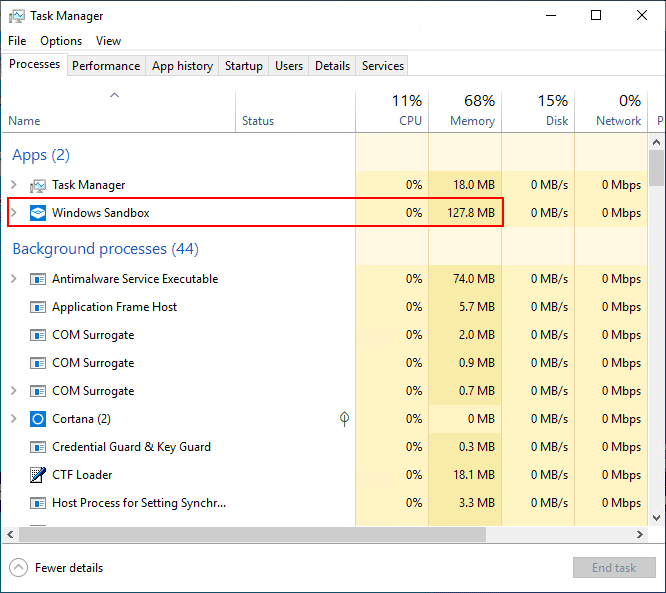
What about resources? This is the awesome part when comparing to running a full Windows 10 VM. As you can see below, the new Windows 10 Sandbox environment is only consuming roughly 128 MB of memory!
What about a test of isolation going the other way? I installed Chrome on the Window Sandbox app host. As you can see, Chrome does not appear in the new Windows 10 Sandbox app environment.
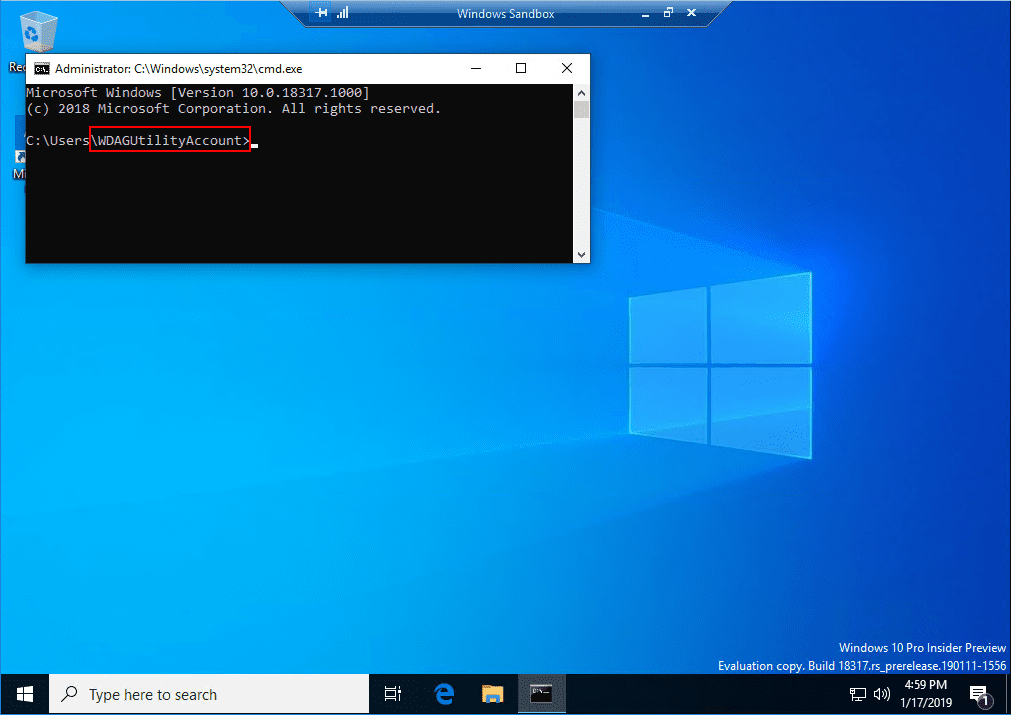
The user account the new Windows 10 Sandbox app is ran under is called WDAGUtilityAccount. What is WDAGUtilityAccount? This account is part of the Windows Defender Application Guard which came with the Fall Creators Update (version 1709). This account is left disabled unless it (Windows Defender Application Guard) is enabled on your device. Obviously it is utilized with the new Windows 10 Sandbox environment.
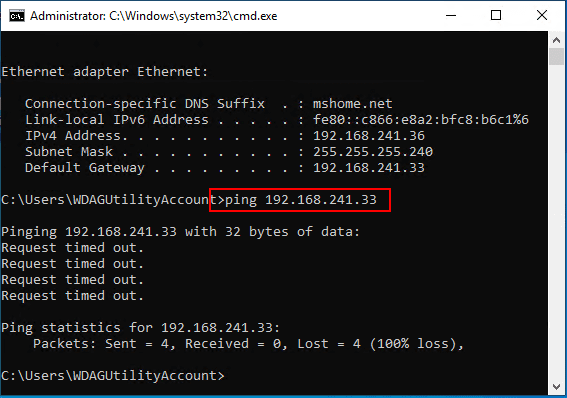
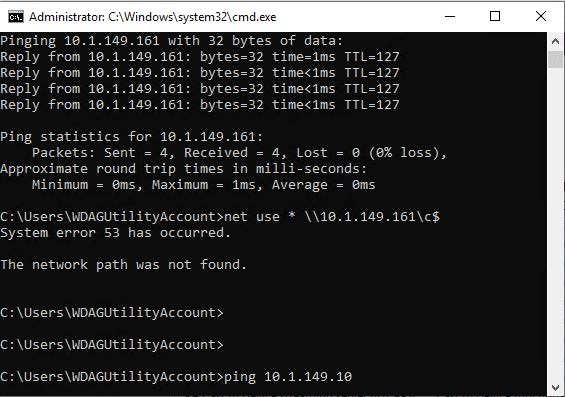
Back to networking for a moment. I wanted to run some tests on pinging between Windows 10 Sandbox and the host and then beyond. At first I could not ping the host/gateway address.
After enabling File and Printer Sharing, I can ping the NAT’ed IP.
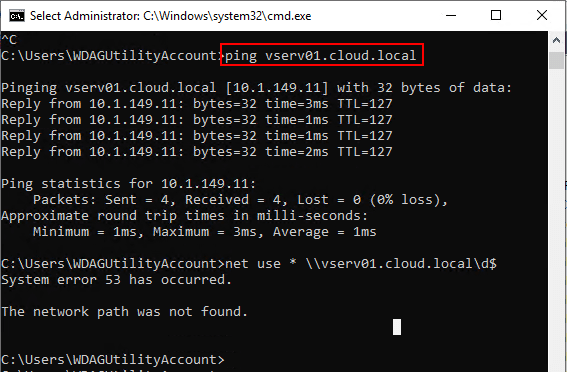
What about the LAN IP address of the Windows 10 Sandbox host? Yes, you can ping it as well after enabling the File and Printer Sharing service on the host.
Can you change your DNS inside the new Windows 10 Sandbox app and ping other hosts on the local network? Yes you can. However, in testing actually mapping a drive, even though the share was enabled, I was not able to map network drives out. This is a good thing, thinking about isolation and the intended purpose of the new Windows 10 sandbox.
Also, a note here is that I could not map a drive to the host of the new Windows 10 Sandbox app.
I have not had time to dig deeper into the specific network settings that are enabled on the new Windows 10 sandbox environment as of yet, but I suspect there is isolated containerized networking at play here that is preventing the drive maps, NETBIOS type traffic, etc. Look for a future post digging a bit deeper into this one.
Takeaways
For me this was a fun exercise – Installing New Windows 10 Sandbox Feature Networking Resources Browsers Security. This is a really killer new feature that from a security perspective is going to be a great new tool. There is no doubt in my mind that security vendors will be able to use this and have hooks into this functionality to perform even more security testing, detonation, etc.
The awesome thing with the new Windows 10 sandbox app is the resource utilization. Thinking about the fact that you no longer have to run a full Windows 10 VM to do basic things such as browsing, downloading files, etc, is going to be a great benefit! What would make this better?
One of the things I think immediately that will be asked and on everyone’s mind is whether or not the “base” Windows 10 Sandbox VM/container can be customized so the default “image” can contain custom applications, i.e. Chrome, etc. There is no doubt going to be great features added to the new Windows 10 sandbox with upcoming builds.