VMware ESXi Successful VM Escape at GeekPwn2018 Security Patch
So VM escape is one of those subjects that has been written about for years and the possibility of being able to access the hypervisor host from within a virtual machine. However, up until just a few days ago, no one had ever successfully “escaped” the VMware ESXi hypervisor to gain root access to the ESXi hypervisor host. This had previously only been successful a few years back in 2009 on VMware’s Workstation product. At this year’s GeekPwn2018 hacking competition held in China, which is a competition for elite hackers to bring to light discoveries and exploits that allow gaining access to systems, the first ever successful VM escape has been carried out on the ESXi hypervisor. In this post we will take a look at VMware ESXi Successful VM Escape at GeekPwn2018 Security Patch and see what we know about how the attempt was successful and what VMware has done about this first successful VM Escape in the wild.
VMware ESXi Successful VM Escape at GeekPwn2018 Security Patch
First, let’s take a look at the details of the successful VM Escape exploit of the ESXi hypervisor. The Geekpwn2018 competition this year unveiled a successful VM Escape of ESXi by a researcher at China-based security firm Chaitin Tech by the name of Zhangyanyu.
An official posting of the VM escape attack has been posted via the Chaitin Tech Twitter account here. A brief tweet with the video states:
Chaitin Tech security researcher f1yyy has escaped VMware EXSi and got root shell on the host for the first time in the world. After demonstrating it at GeekPwn 2018, f1yyy received the Best of Tech Award and was selected to the GeekPwn Hall of Fame
The anatomy of the successful VM Escape comes down to the VMXNET3 virtual network adapter. On the official VMware advisory page found here, VMware describes the issue: “VMware ESXi, Fusion and Workstation contain uninitialized stack memory usage in the vmxnet3 virtual network adapter. This issue may lead to an information leak from host to guest. The issue is present if vmxnet3 is enabled. Non vmxnet3 virtual adapters are not affected by this issue.”
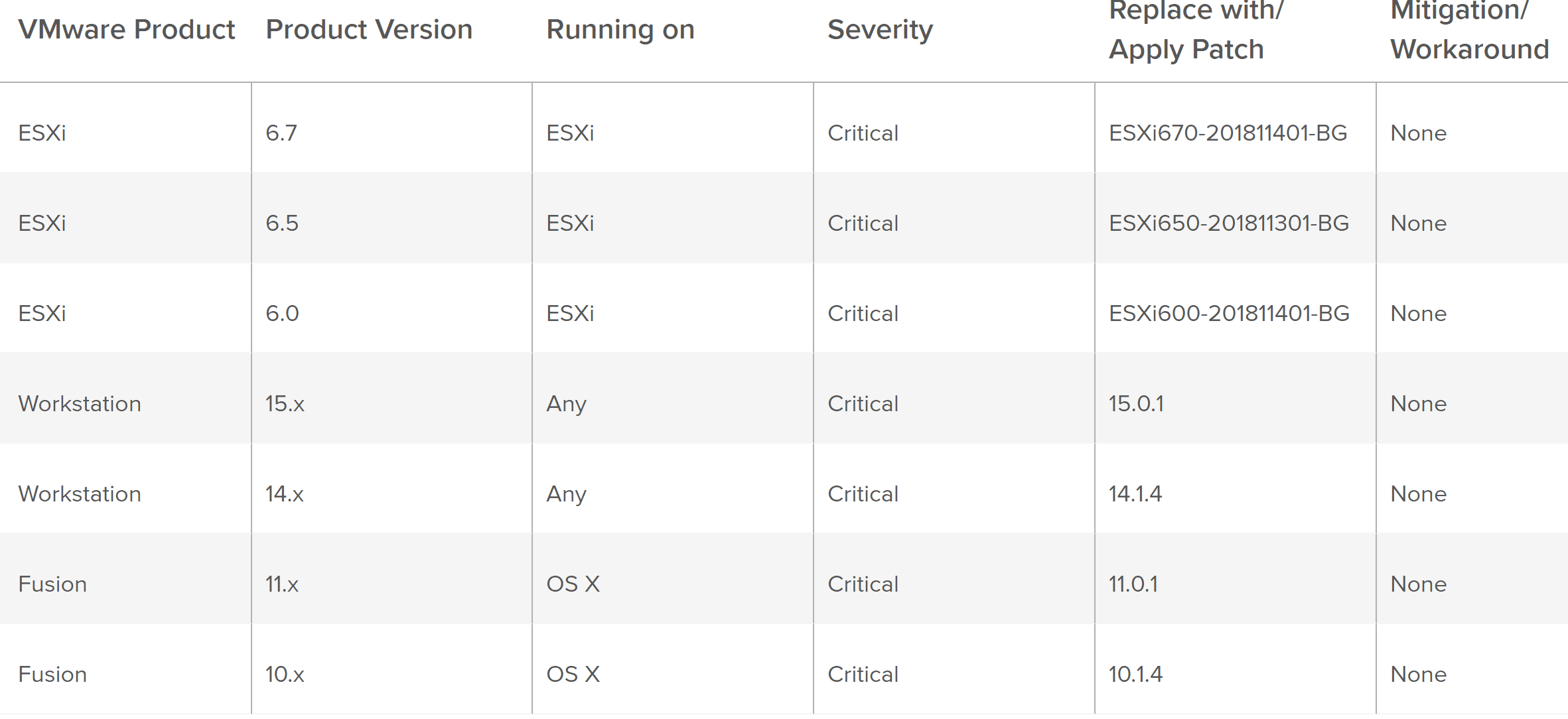
As mentioned, this looks to affect all VMware hypervisor products:

The official CVEs assigned are CVE-2018-6981 and CVE-2018-6982. They are broken out as follows:
A remote user on the guest system can exploit an uninitialized stack memory usage in the vmxnet3 virtual network adapter to gain elevated privileges on the host system [CVE-2018-6981]. Systems with vmxnet3 enabled are affected.
A remote user on the guest system can exploit an uninitialized stack memory usage in the vmxnet3 virtual network adapter to cause information to leak from the host to the guest domain [CVE-2018-6982]. Systems with vmxnet3 enabled are affected.
These are certainly very real and very critical vulnerabilities as it appears that all the remote user needs is remote access to the guest virtual machine and be on a virtual machine that is enabled with a VMXNET3 virtual network adapter.
The relative patches and download links for the various VMware products are as follows:
ESXi 6.7
Downloads:
https://my.vmware.com/group/vmware/patch
Documentation:
https://docs.vmware.com/en/VMware-vSphere/6.7/rn/esxi670-201811001.html
ESXi 6.5
Downloads:
https://my.vmware.com/group/vmware/patch
Documentation:
https://docs.vmware.com/en/VMware-vSphere/6.5/rn/esxi650-201811001.html
ESXi 6.0
Downloads:
https://my.vmware.com/group/vmware/patch
Documentation:
https://docs.vmware.com/en/VMware-vSphere/6.0/rn/esxi600-201811001.html
VMware Workstation Pro 14.1.3
Downloads and Documentation:
https://www.vmware.com/go/downloadworkstation
https://docs.vmware.com/en/VMware-Workstation-Pro/index.html
VMware Workstation Player 14.1.3
Downloads and Documentation:
https://www.vmware.com/go/downloadplayer
https://docs.vmware.com/en/VMware-Workstation-Player/index.html
VMware Fusion Pro / Fusion 10.1.3
Downloads and Documentation:
https://www.vmware.com/go/downloadfusion
https://docs.vmware.com/en/VMware-Fusion/index.html
Overall Security Problem
I really like how Mike Foley summed up the major security risks that are plaguing IT today by focusing in on the culprit of compromises in most cases – people and flawed practices. In Mike’s VMescape.com expose on this issue he sums up the major security threat that he calles “Admin Escape” well:
That’s when your administrator with all of the privs (because nobody actually implements least privilege!) gets compromised and the bad guys walk in through the front door. That’s aproven method of attack. It works all the time. It’s cheaper and far more effective. All this talk about VM Escape is a distraction from the real and proven challenges that face IT Security.
Every major breach in the past 5 years has NOT been via a VM Escape but via poor IT and security practices. Protecting a database with the password “password” or storing sensitive data, unencrypted, on Amazon S3 or having an IT process in place that DISCOURAGES running newer software that mitigates many issues that you are concerned about.
The problem is people. Not technology. Technology is relatively easy to fix. A broken process is MUCH harder to address.
Takeaways
The recently found VM Escape bug in the VMXNET3 network adapter is very concerning and is certainly something that VMware vSphere administrators want to give immediate attention to. The VMware ESXi Successful VM Escape at GeekPwn2018 Security Patch has already been issues by VMware and looks to be a patch that is applicable across the board with all the VMware hypervisor products including even the latest ESXi 6.7 hypervisor all the way down to the VMware Workstation product. Essentially anything that makes use of the VMXNET3 network adapter is going to be in scope here. This helps to shed light on the bigger security issues that exist in many organizations today. Not only do businesses need to ensure they are running the latest patches from a hypervisor standpoint as well as guest operating system standpoint, they need to evaluate and scrutinize processes, access permissions, and overall security vulnerabilities in the environment to ensure their data is safe and secure from attackers.