One of the powerful security mechanisms that we hear about in today’s infrastructure is microsegmentation. Microsegementation is talked about a lot with VMware NSX and other software-defined network technologies that are on the market. VMware NSX is extremely powerful and provides powerful capabilities to ensure that only the devices on the network that need to “talk” to virtual resources are able to communicate. Why is this a big deal? Even with dividing up a network with multiple VLANs, unless no other mechanism is used, all the devices on that particular broadcast domain will be able to communicate by default. From a security standpoint, this is not good. Additionally with today’s stringent compliance regulations, organizations must be able to show that network connectivity is being controlled to the degree necessary. VMware NSX can be used to control access to/from physical resources such as clients that are able to connect to specific servers in the VMware environment. However, what about physical device to physical device connectivity? What about two workstations on the same VLAN? In this type of scenario, this would be outside the boundary of what NSX or other software-defined network technologies are able to control. Let’s take a look at physical device microsegmentation with Extreme Networks Policy to see how using Extreme Networks policy enabled switches and APs, physical devices can be effectively microsegmented from one another.
Understanding Extreme Networks Policy
Extreme Networks Policy implementation provides powerful capabilities to be able to control network traffic in your environment. It does this by implementing role-based policy that allows controlling Quality of Service, protocols, IP addresses, VLANs, authentication, and many other aspects of network communication with network clients that are connected. Traffic can be controlled and manipulated accordingly. The great thing about the policy implemented by Extreme along with Network Access Control is that control can be defined based on a number of different factors, including the type of network a user is logging into (wired or wireless), as well as location based control, and a whole number of other metrics to define the policy applied. This gets into Policy along with NAC which we will cover in a later post. For context here, we are simply talking about Policy.
There are many different ways to assign Extreme Policy in the network. These include:
- Physical ports
- MAC addresses
- IP addresses
- VLAN tags
- RADIUS authentication
This control and manipulation of network traffic provides many benefits including:
- Microsegmentation
- Enhanced security
- Drastically reduced attack surfaces
- Controlled access and priority on traffic
- Traffic can be controlled based on types
Extreme also provides a fully-featured NAC or Network Access Control solution that allows controlling network traffic based on various health type metrics and other advanced implementations of policy. We won’t cover that in this particular post, but look for that in the near future.
Extreme Policy is implemented in a Role Based Access Control mechanism that allows creating rules, placing the rules into services and then adding services to Roles. The roles can then be assigned statically to a port, dynamically using RADIUS, or using NAC/RADIUS. In this walk through, I will simply be statically assigning policy to the physical switchport the client device is connected to.
Physical Device Microsegmentation with Extreme Networks Policy
In this lab scenario, I have an Extreme x440-G2 switch which is a policy enabled Extreme switch. The switch has been added to the Extreme Management Console, which is the management platform that allows centrally managing Extreme and other vendor devices. Finally, I have a physical Windows 10 Pro client that is plugged into a port on the x440-G2 switch.
So for the test, I want to do the following:
- Block the workstation from seeing any clients on the network, besides the ones I allow
- Even if on the same VLAN
- Block the workstation from connecting to any other clients/ports on the Internet
- Still be able to access the client via RDP from select Admin Workstation
To do the above:
- I setup a couple of simple services with simple rule(s) in each service.
- Then, I created a role and added the services to the Role.
- The role was then applied to the switchport of the physical client.
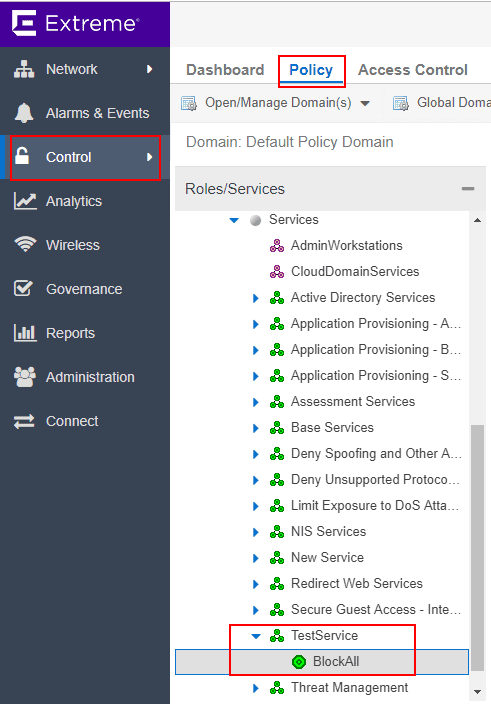
For Extreme Policy, creating the policies generally follows the above workflow with creating the required components. To access the Policy dashboard, I login to Extreme Management Center.
Navigate to Control > Policy. Here is where we create new Services, rules, and Roles. Also, this is the area that policy is assigned to switches, ports, etc. Below, I have created a new TestPolicy service that contains a single rule. I am going to block traffic using this rule. Rules are processed like ACLs from the top down.
The Traffic Description is where you classify the traffic that is to be controlled/manipulated. To block all traffic, I am setting the Type to Ethertype and the Value to IP. The Access Control drop down is set to Deny Traffic.
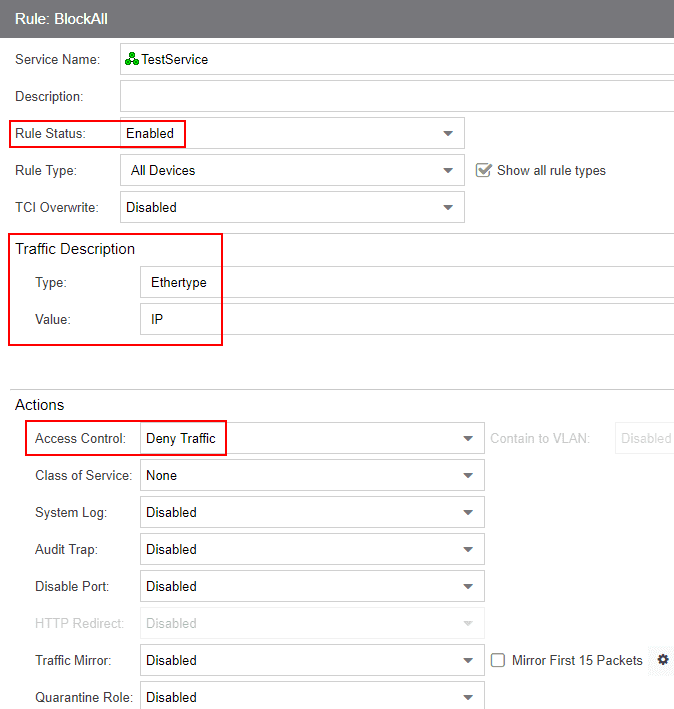
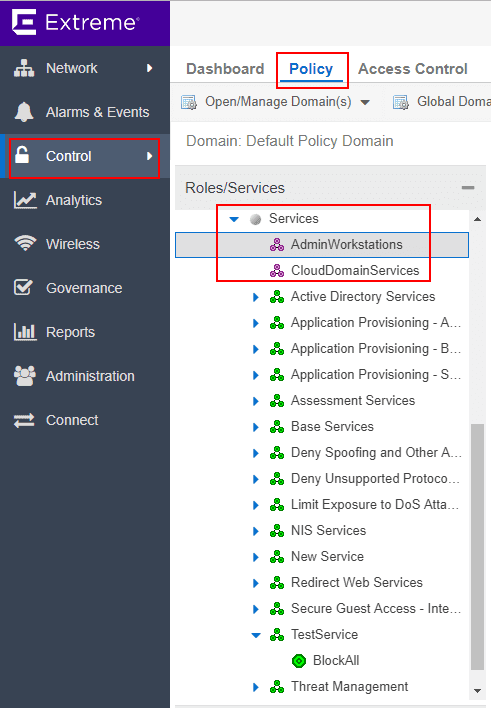
Next, I create two new automated services which allow adding network resources which are groupings of IP addresses.
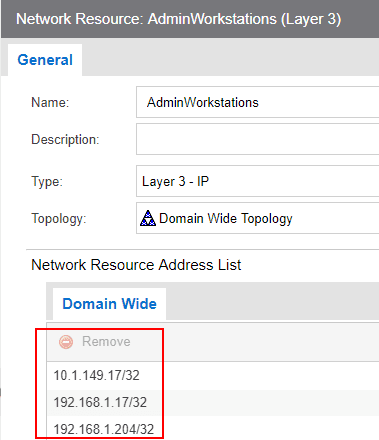
Under the Network Resource, you can add multiple IP addresses to the resource. Here I have added the IP addresses of my administrative workstations.
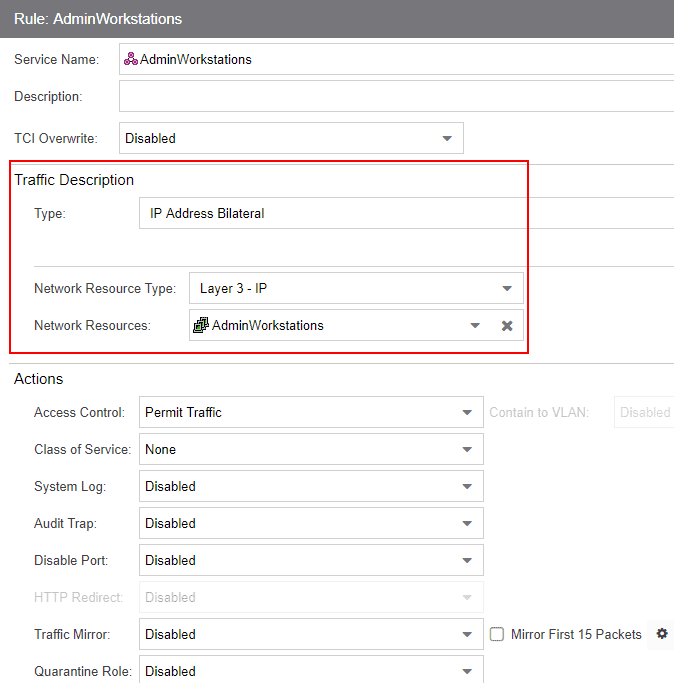
In the automated service, I am using the Network Resources defined in the step above. I have set the Access Control to Permit Traffic to allow the traffic through.
Back under the Roles heading, here is where you create new roles and add services. I created a new Role called TestPolicy. I then added the services that were created in the above steps.
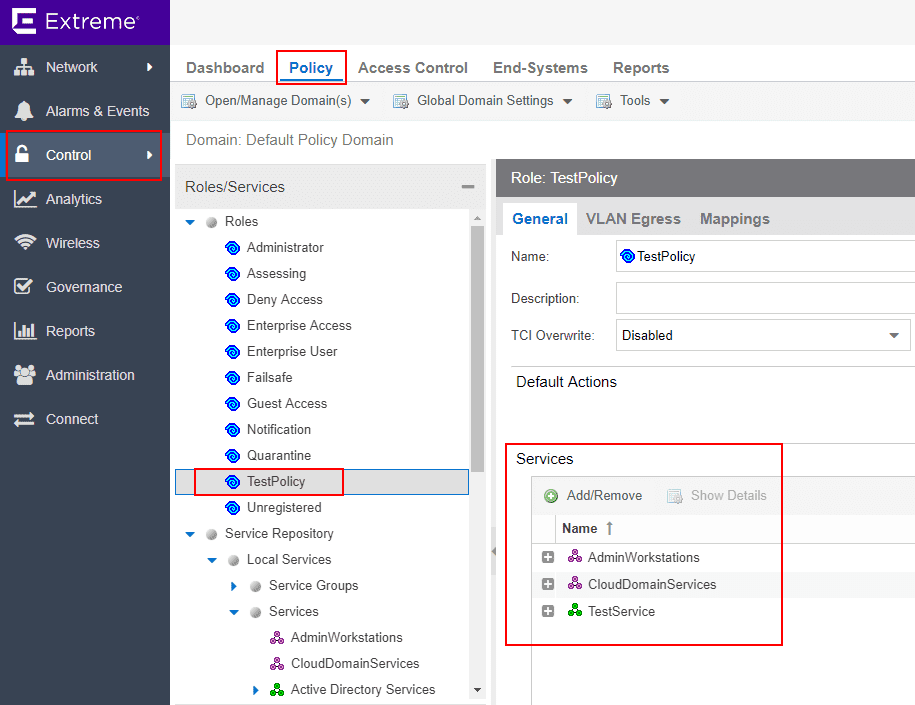
Before applying the policy, you can see I am able to ping out from the physical client.
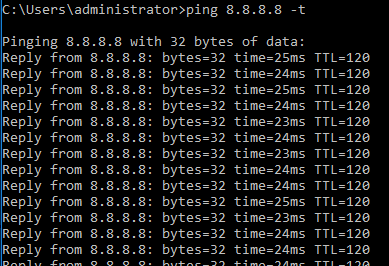
Next, I assign the policy to the port the physical client is connected to.
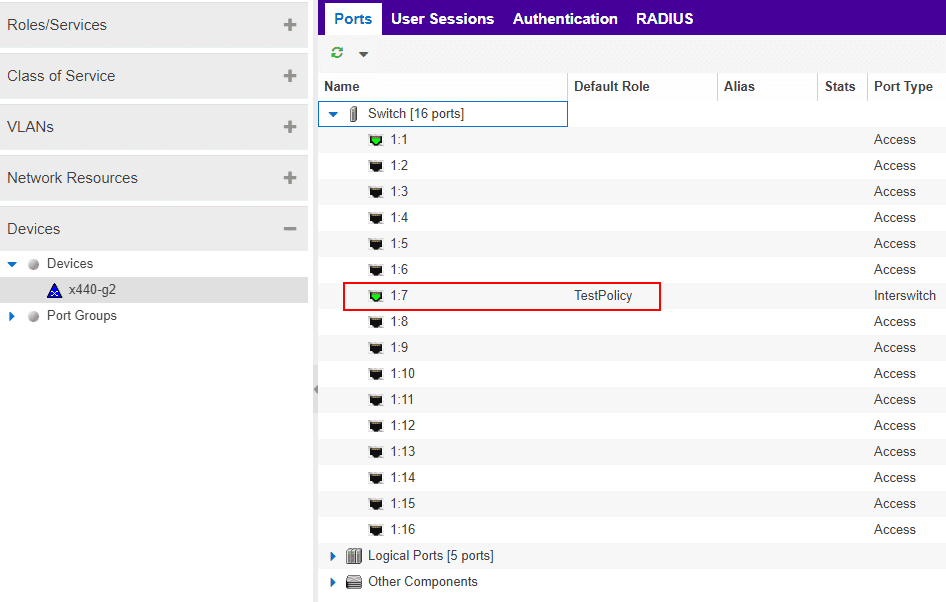
As soon as the policy is applied, pings start dropping. Also, pings to other hosts in the same VLAN fail as well.
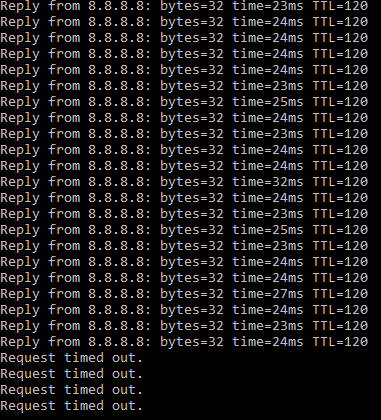
As a result of applying the policy, I still have connectivity from/to my administrative stations as well as my domain controller, but all other traffic is being dropped, including traffic to other nodes on the same subnet.
Extreme Networks Integrates with SDN
A note here about SDN and Extreme Networks. When choosing the Extreme Networks solution, it is not a matter of choosing physical networking or SDN. While the scope of this discussion is concerning securing physical devices, choosing Extreme for securing the physical side does not mean you have to choose one or the other. Extreme Networks has really nice integration with VMware’s NSX platform via their datacenter line of products. Even in the x460-G2 class switches, which are the top-tier edge product at the time of this writing, the switches can act as VXLAN enpoints, meaning you have the ability in the physical network to interact directly with NSX VXLAN networks. The Extreme solution simply extends role based policy control out to physical network devices which can greatly augment an SDN implementation.
Takeaways
Extreme Networks provides a powerful mechanism for network access control and traffic manipulation. Physical Device Microsegmentation with Extreme Networks Policy is easily accomplished using a policy-enabled switch, Extreme Management Center and creating services, rules, Roles, and then applying the role to the device, either with static policy (demonstrated above) or with dynamic policy that can be accomplished using RADIUS or NAC and RADIUS together. The complexity of today’s security requirements and client devices often requires multiple solutions to fully accomplish the intended result. VMware NSX and other software-defined solutions are powerful and are certainly the way to go with virtual environment microsegmentation. However, there are use cases and scenarios where being able to do this at the physical switchport are certainly desirable such as in the case of securing traffic between workstations. The integration from the Extreme side with VMware NSX is certainly powerful as well. Stay tuned for more posts covering Extreme Networks policy and network access control as we delve deeper into this functionality.
Google is updating how articles are shown. Don’t miss our leading home lab and tech content, written by humans, by setting Virtualization Howto as a preferred source.