MineMeld Threat Intelligence Installation in VMware vSphere
Threat intelligence and threat “hunting” in today’s enterprise datacenter is one of the top priorities among IT engineers. Security is an ever growing concern that organizations are spending major money on. In order to prevent cyberattacks from affecting their environments, many organizations collect what is known as Indicators of Compromise or (IOCs) that provide intelligence gleaned from various threat intelligence providers. Palo Alto networks makes available an open-source application called MineMeld that intelligently aggregates and streamlines the threat intelligence and threat hunting process. In this post, we will look at MineMeld Threat Intelligence Installation in VMware vSphere and look a bit closer at what MineMeld is and the installation process in VMware vSphere.
What is Palo Alto MineMeld?
Palo Alto describes MineMeld is self described as an extensible Threat Intelligence processing framework and the ‘multi-tool’ of threat indicator feeds. It is an extremely flexible tool that allows collecting, aggregating and fltering indicators from many different sources and making them available for use for a variety of providers or Palo Alto Networks security platforms. The cool thing about MineMeld is that it is open source and is contributed to as such.
MineMeld uses three different entities that it calls “nodes” to automate the flow of indicators from source to destination. They include the following:
Miners – Extract indicators from sources of threat intelligence such as threat indicator feeds or services like Palo Alto AutoFocus
Processors – These receive indicators from miners and manage these indicators by providing the ability to aggregate them together, eliminate duplicated indicators, and merge together different sets of metadata for the same indicator.
Outputs – These receive indicators from processor and format them in a way to allow MindMeld to dynamically send the indicators to one or multiple destinations. This can be to a threat intelligence platform like Palo Alto’s AutoFocus or to the firewall itself.
MineMeld Threat Intelligence Installation in VMware vSphere
To install MineMeld, I followed the steps found here in the official documentation to manually provision MineMeld on an Ubuntu 14.04 server (14.04 is the only Ubuntu version mentioned in the docs, haven’t tested whether the packages are available for 16.04 LTS, etc).
After manually spinning up an Ubuntu 14.04 LTS server in my VMware vSphere ESXi lab environment, I followed the installation steps very closely from the official walkthrough and things went as expected, no issues, and the commands all completed successfully. Take a look at the steps to install here: https://live.paloaltonetworks.com/t5/MineMeld-Articles/Manually-install-MineMeld-on-Ubuntu-Server-14-04/ta-p/98454
In the screenshots below, I have consolidated a couple of the steps for showing the process.
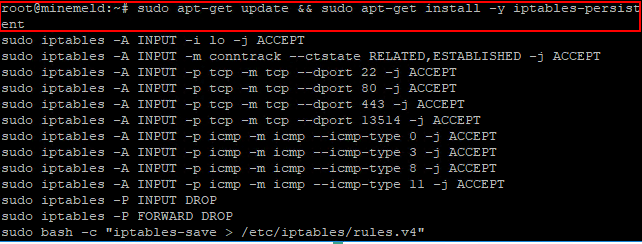
Step 1 – Setup IP Tables
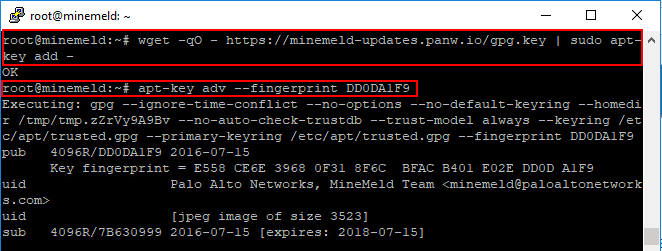
Step 2 – Adding the GPG key and Checking the Signature
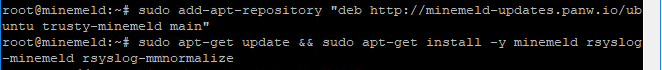
Step 3 – Adding the APT repo and installing MineMeld
Step 4 – Check to see if MineMeld is running
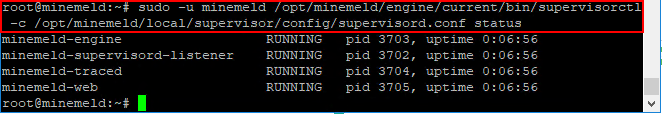
MineMeld
Let’s take a look at a quick walk through of the interface and a few areas to note. The interface is really slick and performs well. Things seem to be pretty intuitively arranged and within a few minutes I was able to find my way around to the different areas and configuration that I needed.
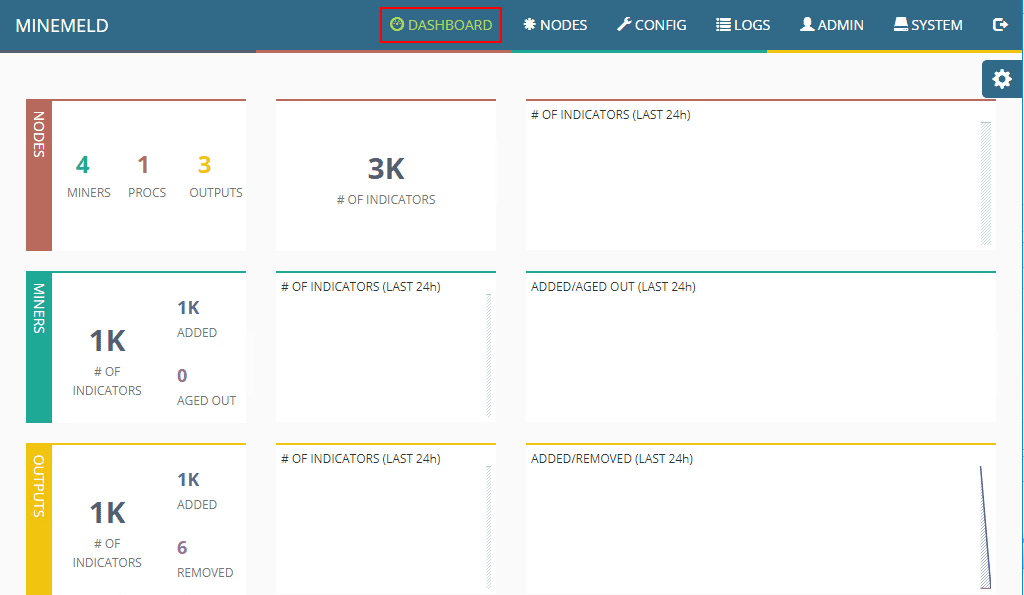
After a few minutes the dashboard starts coming to life and the feeds are pulled in, etc.
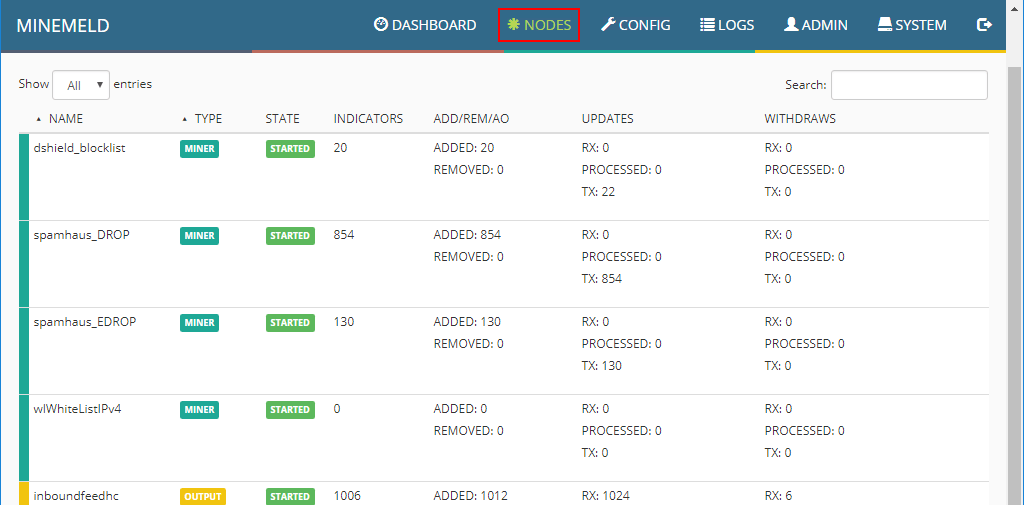
Under the nodes menu, you can see the default nodes that are preinstalled with MindMeld including miners, outputs, and processors.
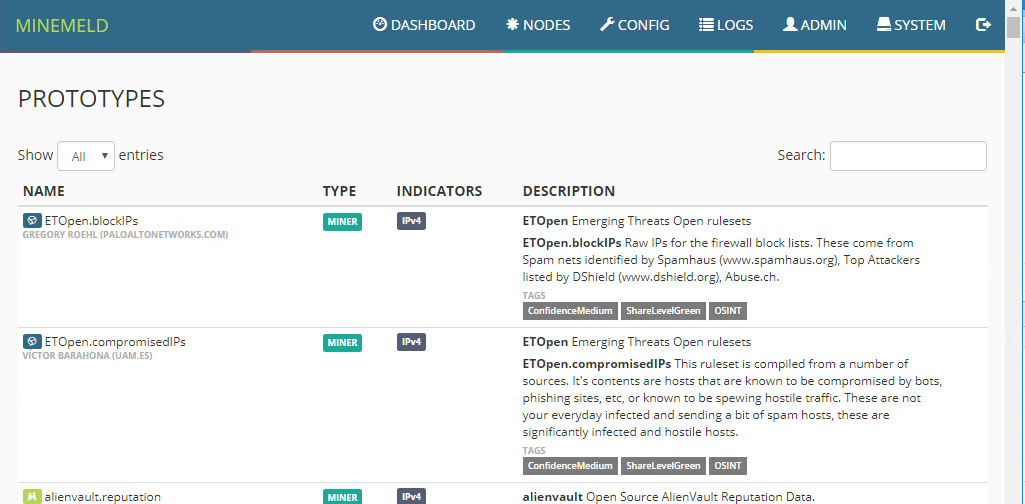
Under the Config menu, you can see and add Prototypes to the MineMeld configuration. Prototypes are new miners that can be imported into the MineMeld configuration. There are tons to be added.
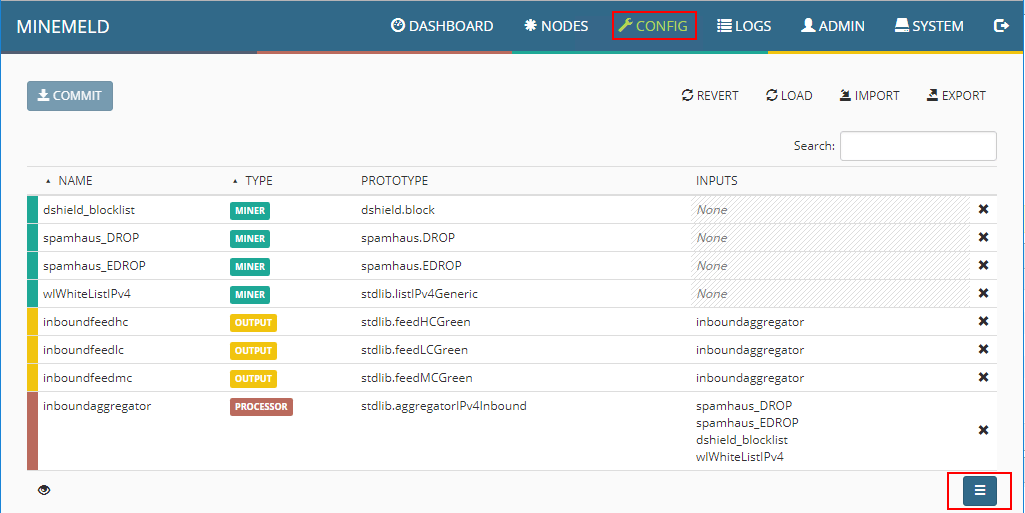
The screen below only shows a handful…however, there are many different prototypes that can be added to the configuration. The Search functionality is also very helpful if you know the name or similar of the prototype you want to add.
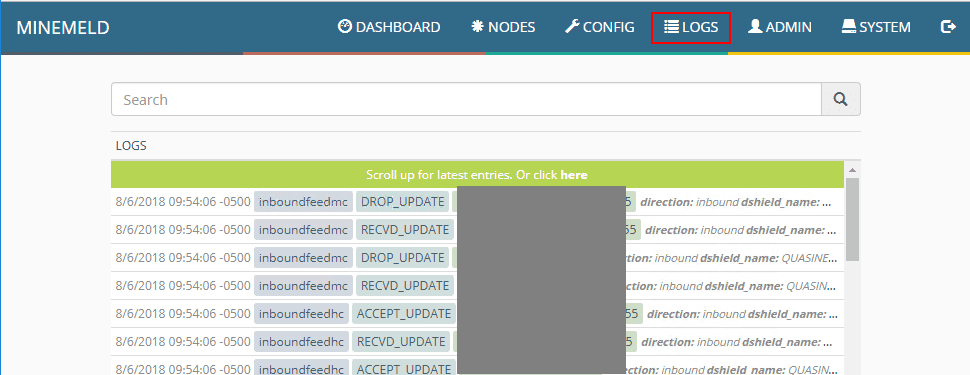
Under the Logs menu, you can see the realtime data that is being aggregated from the installed miners.
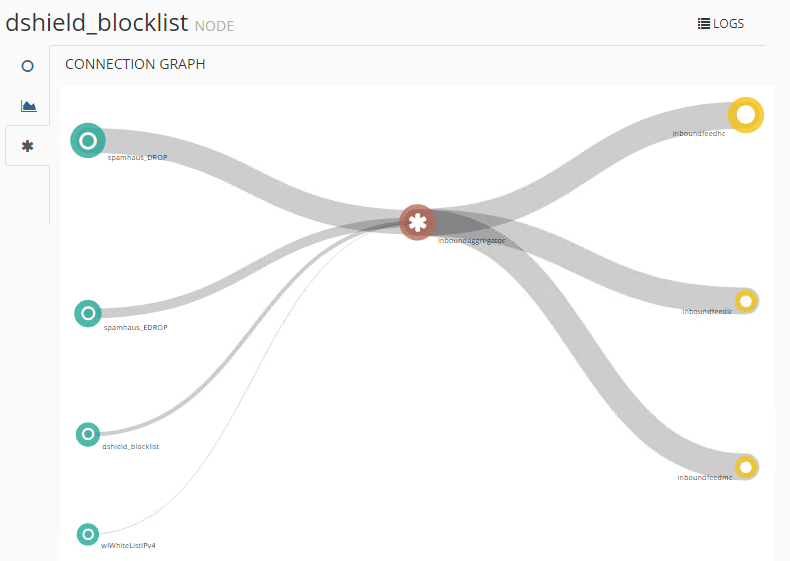
MineMeld connection graph showing some of the default config connection information.

Takeaways
If you are wanting to dive deeper down the rabbit hole of threat intelligence and threat hunting and remediation, a great tool to start getting your feet wet is the MineMeld utility that is a free download. I found the installation was extremely easy with the documented steps and running this in an Ubuntu 14.04 VM inside of VMware vSphere worked as expected – rock solid. I am looking forward to integrating this tool into the home lab and network intelligence that I already have in place. Stay tuned for more posts and information along the way covering MineMeld and further configuration.







