Managing Windows Servers with Ansible is a powerful way to perform configuration management and to remediate configuration skew in a server environment. As we have already explored basic Windows Server automation with Ansible and how to bootstrap Windows Server configuration with Ansible playbooks, let’s take this a step further with how to configure Ansible Windows Server Kerberos authentication in Ubuntu. We will look at what components need to be installed in Ubuntu as well as how the configuration for Kerberos is made in Ansible to utilize Active Directory for connecting via WinRM.
General Ansible WinRM Connectivity
In general, to get Ansible working with WinRM, you need to run the ConfigureRemotingForAnsible.ps1 script that is found here: https://github.com/ansible/ansible/tree/devel
How do you run this command remotely? There are a couple of ways. You can use PSEXEC to do this:
psexec \myserver -accepteula -nobanner -s -u DOMAINAdministrator powershell -ExecutionPolicy Bypass -Command "iwr https://raw.githubusercontent.com/ansible/ansible/devel/examples/scripts/ConfigureRemotingForAnsible.ps1 -UseBasicParsing | iex"
Solarwinds also has a really neat FREE utility for remotely enabling WinRM on remote Windows Servers: https://www.solarwinds.com/free-tools/remote-execution-enabler-for-powershell
Why Use Kerberos Authentication?
Why use Kerberos authentication with Ansible? If you are managing many server resources in a large environment especially, there are certainly advantages to using Kerberos authentication with Windows Server environments as you leverage the central user authentication that Active Directory supplies to configure and manage your Windows Server resources. There are also trust advantages with WinRM that are built in when using Active Directory credentials. As you will see below, the mechanism to pass the AD credentials with Ansible to the Windows Servers is a bit cumbersome with the kinit command. However, I still like how the password is handled at this point with a Kerberos ticket instead of a password that is stored or using Ansible vault for YAML files.
Ubuntu Components for Ansible Kerberos Authentication
The following components and order of listing is how I was able to get a successful implementation of Kerberos working in Ubuntu 16.04 LTS.
- sudo apt-get install gcc python-dev libkrb5-dev
- sudo apt-get install python-pip
- sudo pip install –upgrade pip
- sudo pip install –upgrade virtualenv
- pip install pywinrm[kerberos]
- sudo apt install krb5-user
- sudo pip install pywinrm
- sudo pip install ansible
Configuring Ubuntu for Kerberos Authentication with Active Directory
After installing the above prerequisites including the following, you should now have access to configure the krb5 configuration file. This file sets up the configuration between the Ansible server and Kerberos/Active Directory “realms”.
- sudo apt-get install gcc python-dev libkrb5-dev
- sudo apt install krb5-user
The file path is:
/etc/krb5.conf
Below is a sample configuration that I have working in my home lab environment for using with Kerberos authentication between my Ansible VM and Windows Server 2016 Active Directory. A key hurdle for me was capitalizing the default_realm and other specific areas of the config file as you see below. The rdns directive can also cause issues in some environments.
[logging]
default = FILE:/var/log/krb5libs.log
kdc = FILE:/var/log/krb5kdc.log
admin_server = FILE:/var/log/kadmind.log
[libdefaults]
default_realm = MYDOMAIN.LOCAL
allow_weak_crypto = true
dns_lookup_realm = false
dns_lookup_kdc = false
rdns = false
ticket_lifetime = 24h
renew_lifetime = 7d
forwardable = true
[realms]
MYDOMAIN.LOCAL = {
kdc = dc1.mydomain.local
admin_server = dc1.mydomain.local
}
Getting a Kerberos Ticket and Listing the Kerberos Ticket
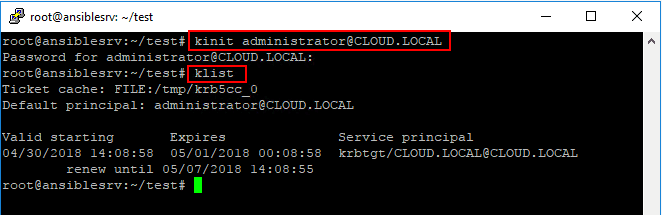
There area couple of really simple commands that we run on our Ansible box to both get a Kerberos ticket and also list our Kerberos ticket to know we have received one:
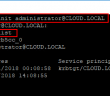
- kinit – get a Kerberos ticket
- klist – list Kerberos tickets
- kdestroy -A – Removes existing Kerberos tickets
As you can see below the syntax for the kinit command, we use the %username% @ UPPERCASE domain name. You are then prompted to enter a password for the account. To see the Kerberos ticket and see when it was issued and when it is set to expire, use the klist command.
Configuring Group Vars for Ansible Inventory to Connect Using Kerberos
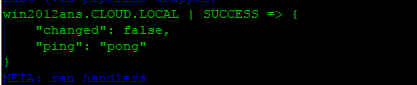
In the group variables section of our config for connecting your Ansible control VM to the Windows Servers it is managing, needs to look something like the following:
ansible_user: [email protected] ansible_connection: winrm ansible_port: 5985 ansible_winrm_transport: kerberos ansible_winrm_cert_validation: ignore ansible_become: false
Notice above that the ansible_user is the user name that we have the Kerberos ticket for. The caveat to the way Ansible handles Kerberos at this point (correct me if I am wrong in the comments section) is there is no way to pass this in without using kinit at least that I have found. The password was already entered to receive the valid Kerberos ticket using the kinit command.
Takeaways
Configuring Ansible for use with Kerberos Authentication is the way to go especially in larger Windows Server environments where you may have hundreds or thousands of servers. By leveraging Kerberos authentication you can easily authenticate against these domain joined resources. If you are using an Ubuntu Control VM for Ansible, loading the prerequisites above, and installing in the order shown, will install the prerequisites that are needed as well as the Ansible modules such as py_winrm needed for connecting to Windows Server resources. All in all using Kerberos authentication with a Windows Server environment that is connected to Active Directory is the way to go for ease of use, security, and overall authentication uniformity.
Google is updating how articles are shown. Don’t miss our leading home lab and tech content, written by humans, by setting Virtualization Howto as a preferred source.