Windows Server 2016 Security Features and Hardening
There is no doubt about it that Windows Server 2016 is Microsoft’s most powerful server operating system. If you have been waiting on reasons to upgrade server infrastructure to Server 2016, security may be among the top reasons why you would want to do so. It touts some of the most advanced new security features released by Microsoft to date. Microsoft has come a long way with Windows in the security realm and the proactive and robust security features of Windows Server 2016 prove the point. Let’s take a look at Windows Server 2016 security features and hardening that make it a great enterprise server operating system from a security perspective.
Windows Server 2016 Just In Time and Just Enough Administration
Controlling privileged access is very important. Attackers look to compromise these highly prized accounts as they represent the ability to do just about anything on a system, especially if it is a domain administrator account. Windows Server 2016 best practices for hardening limits allows privileged access to be controlled by restricting what an account can do and when the account can do it. There are a couple of technologies that allow this type of credential management:
- Just Enough Administration (JEA) – JEA – Comes preinstalled and provides a generic role based access control system to provide RBAC control. A JEA endpoint is configured by a trusted administrator to give access to all the commands that a particular user needs to perform tasks. Using the builtin capabilities of PowerShell remoting the non-privileged user account is authenticated and JEA runes the Windows PowerShell commands you specify by using an elevated virtual account on the targeted computer. Windows Management Framework 5.0 is required (Windows 2008 R2 and higher)
- Just In Time Administration (JITA) – Using this technology, administrators are no longer an administrator in a perpetual way – 24×7 around the clock, etc. Access will be granted for the specific time it is needed. Using Local Administrator Password Solution or Microsoft Identity Manager 2016, organizations can deploy the JITA workflows.
Optimized Windows Defender for Windows Server 2016
Windows Defender has been included in Windows since Windows 8. However with this version of Windows Defender, it has been optimized for Windows Server and is enabled by default now. Also, it provides the engine for many of the underlying new security features in Windows Server 2016. Windows Defender in Windows Server 2016 provides the following:
- Virus, malware, and spyware protection and removal
- Boot time protection
- Real-time protection
- Cloud-based protection
- Network inspection and protection
- Free automatic updates
Enterprise admins will love the fact that Windows Defender can be configured via Group policy, PowerShell, WMI, or with the GUI in Windows Server 2016.
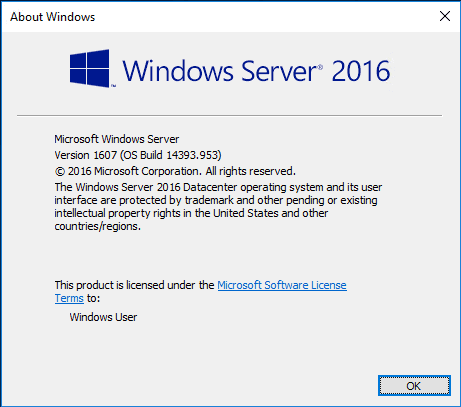
Windows Server 2016 Credential Guard
Windows Server 2016 Credential Guard uses virtualization based security technology in Windows Defender to encrypt secrets. Examples of this would be NTLM password hashes, Kerberos tickets, stored app credentials. This ensures that only privileged system processes can access and make use of the secrets. This helps to protect against attacks such as Pass-the-Hash or Pass-The-Ticket. Windows Defender is no on by default in Windows Server 2016 and has been optimized for the server operating system. The great thing is that by default in the server operating system there is now an anti malware platform configured and screening.
The Credential Guard is easily configured in Windows Server 2016 via a policy setting. To turn on Credential Guard via the Virtualization Based Security setting, navigate to group policy settings for the local server Computer Configuration >> Administrative Templates >> System >> Device Guard and

Additionally, starting in Windows 10, version 1607, Remote Credential Guard allows protecting your credentials over a Remote Desktop connection by redirecting Kerberos requests back to the device that requesting the connection. If the target remote desktop server is compromised, your credentails are not exposed because they are never passed over the network to the target device. To enable Remote Credential Guard in “pre-1703” there is a registry key:
reg add HKLMSYSTEMCurrentControlSetControlLsa /v DisableRestrictedAdmin /d 0 /t REG_DWORD
However, in 1703 and newer, you can use group policy to configure. computer Configuration >> Administrative Templates >> System >> Credentials Delegation
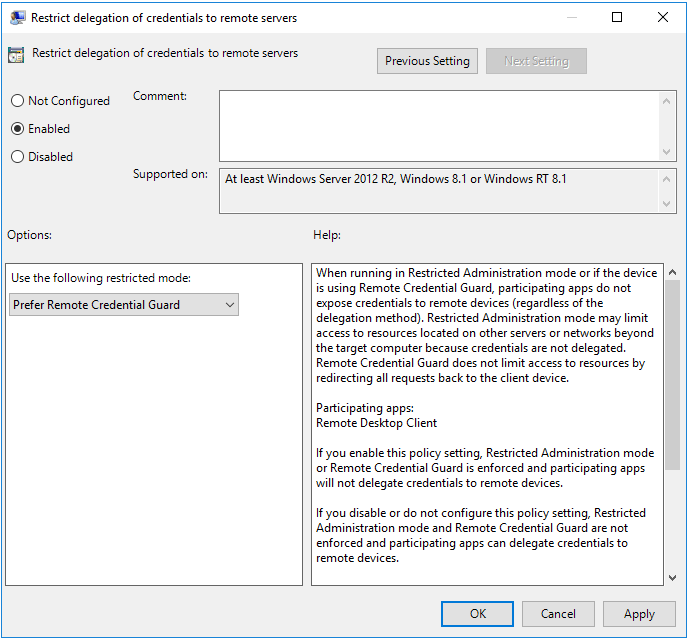
Also, to enable remote credential guard for a specific connection, you can specify this in the Remote Desktop Connection:
mstsc.exe /remoteGuard
Windows Server 2016 Control Flow Guard
This is a new option built into Windows Server 2016 that helps to protect the operating systema dn applicControl Flow Guard – Allows you to block threats for unknown vulnerabilities. CFG makes sure that even if an attacker tries to exploit, CFG blocks known attack vectors from unknown vulnerabilities. This is also included in Visual Studio so developers are able to turn this option on for custom applications.
Windows Server 2016 Device Guard
Windows Defender Device Guard augments the AppLocker featureset by allowing the ability to specify which binaries are authorized to run on your server including user mode and kernel mode binaries. This is accomplished by creating a code integrity policy to define which apps can run on your system, effectively blocking malicious code. This helps to prevent:
- Infection by new malware that has no malware signature
- Unsigned code
Malware that infects the kernel
Deployment guide for Device Guard can be found here.
Windows Server 2016 Security Resources
Security and Assurance in Windows Server
Windows Security Blog
Windows Server 2016 Security Guide
Thoughts
It is so nice to see that Microsoft has security at the forefront of new Windows Server operating systems. The new Windows Server 2016 Security Features and Hardening certainly shows that to be the case. Windows Server 2016 has a number of great new security technologies that are included in the box. No longer are administrators left with a bare, unprotected server out of the box. The tools and software are there and much of which are already on by default.