When thinking about security, security hardening is one of the terms we use to describe what we do to reduce the attack surface of a host to make it more difficult for it to be compromised in an attack. There are several recommendations that we can implement to reduce the attack surface in VMware ESXi to make sure the host is “hardened” from the security standpoint. Let’s take a look at recommendations in how to security harden VMware ESXi hosts and the steps involved to do this. They include the following:
- Disabling services in the ESXi firewall
- Change default account access
- Adding a VMware ESXi host to a directory service
- Apply permissions to the ESXi hosts using host profiles
- Enable Lockdown Mode
- Control access to hosts (DCUI/Shell/SSH/MOB)
Enable Configure Disable services in the ESXi firewall
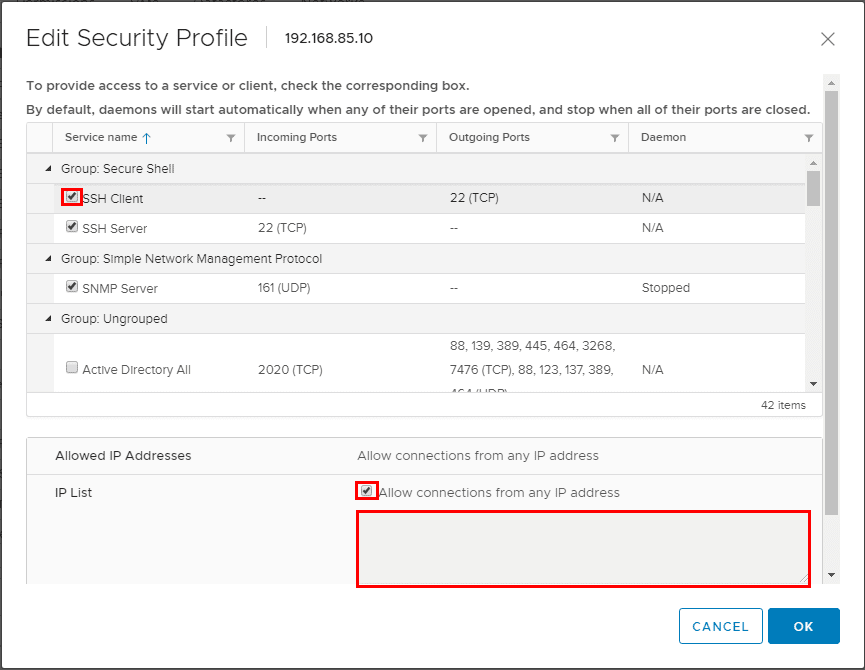
The VMware ESXi host firewall is a pretty powerful means of scoping down access to various services, disabling services, and configuring services and their access. You can even control from a network standpoint end user devices that are able to connect to various services on a per service group level in the ESXi firewall. When security hardening VMware ESXi hosts, the fewer services that need to have firewall access the better. Also, for those services that need to have connectivity, scoping access from a network standpoint is desirable.
By using the “checkboxes” to the left of each service, you can quickly enable or disable services and their ports “poked through” the firewall. Also, you can set the Allowed IP Addresses that are able to connect to each service port. By default, the Allow connections from any IP address is selected. If you deselect this checkbox, you can specify specific IP addresses that are able to connect to a particular service. These can be in the form of subnets, IPs, etc. You can comma separate them.
Change Default Account Access
By default, ESXi hosts have a few default accounts that are used for various things. Most are familiar with the “root” user that is used to join vCenter Server, etc. The root user is a very desirable account from an attack perspective as it has administrative permissions on the ESXi host and great damage can be wreaked on a host with this account. The root account if used should have a very complex password assigned. Permissions for root can be changed from the administrator role as long as you have another administrator role assigned to a named user. I would not recommend deleting the root account as this can lead to issues. It is a better approach for auditing adminstrative actions to use named accounts for administrators accessing the host and performing any actions at that level.
The default roles available for a VMware ESXi host are fairly limited:
- Administrator
- Read-Only
- No Access
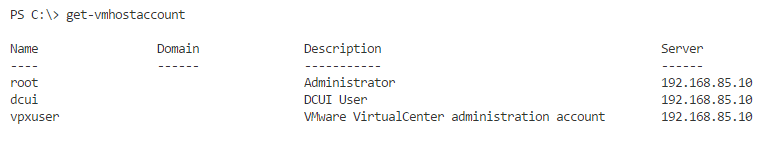
There are three users that are created by default on a VMware ESXi host:
- root
- vpxuser
- dcui
You can use PowerCLI to list the local VMware ESXi local user accounts:
Get-VMHostAccount
Adding a VMware ESXi host to a directory service
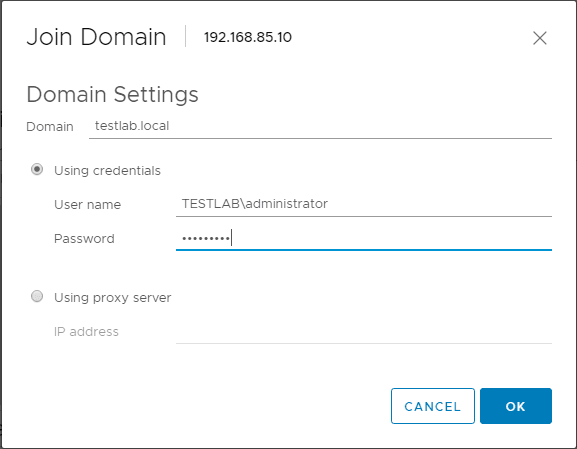
Most organizations are utilizing Microsoft’s Active Directory services as the centralized authentication source for the enterprise datacenter. By joining our VMware ESXi host to Active Directory, we are centralizing the local user accounts with Active Directory instead of having to create the same local user account on multiple VMware ESXi hosts. This greatly simplifies managing ESXi local user accounts. It also aligns ESXi host password management with Password policies that are established with Active Directory and makes sure company password policies extend down to the underlying VMware vSphere ESXi host infrastructure. There is a special group called ESX Admins that is utilized to establish administrative permissions on the ESXi host. Make sure this group is created in Active Directory before joining your ESXi hosts to AD.
Using the HTML5 client, navigate to Configure >> System >> Authentication Services >> Join Domain
You can also make use of PowerCLI to join the ESXi host to an Active Directory domain:
Get-VMHost | Get-VMHostAuthentication | Set-VMHostAuthentication -Domain $domain -User $username -Password $password -JoinDomain
Apply permissions to the ESXi hosts using host profiles
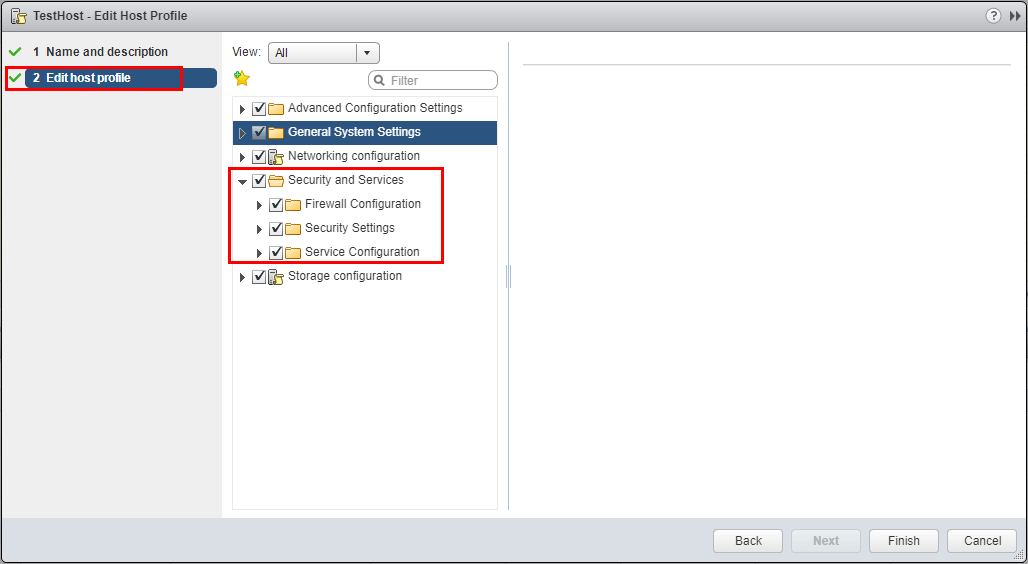
Host profiles are configuration management at the host level. They allow maintaining configuration consistency and correctness across the datacenter. Host Profiles eliminate having to configure everything by hand and are able to capture configuration including networking, storage, security and other settings. Having consistent configuration is very important as relates to security. However, another important benefit that host profiles bring to the mix is the ability to monitor for host configuration errors and deviations. Host profiles can monitor for host configuration changes and ensure the hosts are brought back into a state of compliancy. This is also key when thinking about security as changes to the host can be caught and remediated. Below, you can see the security configuration contained within the host profile.
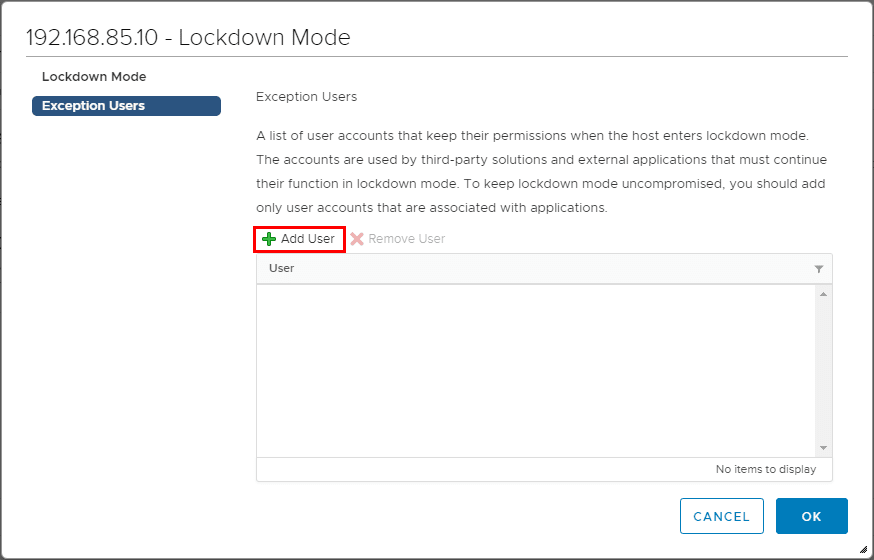
Enable Lockdown Mode
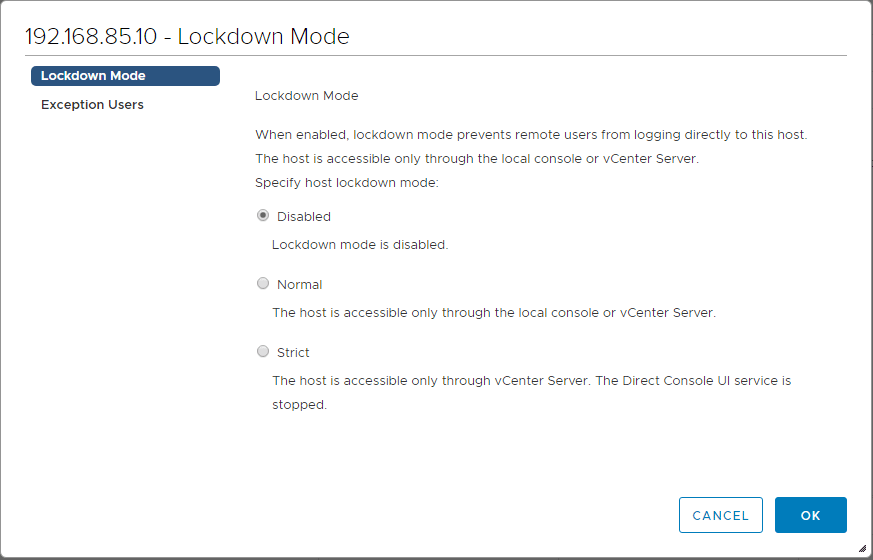
Lockdown mode is a great way to increase the security stance of a VMware ESXi server. Lockdown moe disables direct communication with an ESXi host and requires the host is managed by vCenter Server. This makes sure the roles and access controls that are implemented at the vCenter Server level are always enforced and someone would not be able to bypass this by simply logging in directly to the VMware ESXi server itself. This helps to minimize the risk of someone getting privileged access outside of permissions assigned at the vCenter level. This helps to centralize access and permissions through vCenter access only.
Note Users who are listed in the DCUI.Access.list are allowed to override lockdown mode and login to the DCUI. By default the root account is the only account listed in this list.
To enable Lockdown mode in the HTML5 UI, navigate to Configure >> System >> Security Profile >> Lockdown Mode >> Edit
To enable Lockdown Mode with PowerCLI, use the following snippet.
Get-VMHost | Foreach { $_.EnterLockdownMode() }
Control access to hosts (DCUI/Shell/SSH/MOB)
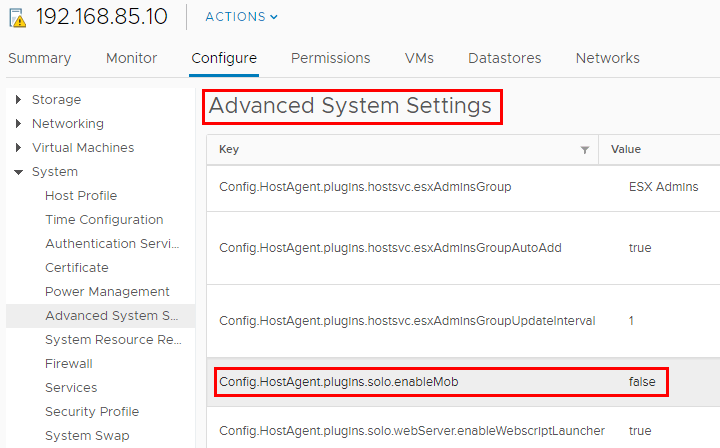
When we control access to hosts and in particular the DCUI, Shell, SSH, and MOB we can further restrict access and security harden our VMware ESXi hosts. We can disable the DCUI by stopping the service or by enabling Lockdown mode. ESXi shell is disabled by default so we want to make sure to keep it that way or tightly monitor to make sure it doesn’t get enalbed. SSH is a service that we often enable and disable, but again, making sure this is controlled via Host Profiles, etc, we can minimize that attack surface. The Managed Object Browser or MOB can be helpful to explore in certain cases, however needs to be disabled for general purposes. Make sure this is disabled here by checking the following advanced configuration setting. If set to false it is disabled. True is enabled.
Thoughts
Hopefully this walkthrough how to security harden VMware ESXi hosts will help anyone looking to create a better security stance in their vSphere environments. By checking the aforementioned items, you can greatly help your security posture and drastically reduce the attack surface in your vSphere environment. Be sure to check the vSphere 6.5 Security Configuration guide for more items that are worth giving attention to throughout any vSphere organzation for better security.
Google is updating how articles are shown. Don’t miss our leading home lab and tech content, written by humans, by setting Virtualization Howto as a preferred source.