What is VMware NSX SpoofGuard
VMware NSX includes many great features that help to bolster an organization’s security posture at a network level. It allows the abstracting of network and security functionality from the underlying physical network infrastructure. We often talk about microsegmentation with VMware NSX and the security benefits that it provides to tiers of applications. A lesser known feature of VMware NSX is SpoofGuard. In this post, we will take a look at What is VMware NSX SpoofGuard and the configuration of this feature in VMware NSX.
What is VMware NSX SpoofGuard?
A tool that attackers often use to penetrate networks is spoofing legitimate traffic on a network so that traffic appears to be coming from a trusted source on a network. This is often referred to as ARP spoofing. The attacker attempts to link a malicious ARP address to a legitimate IP address.
With VMware NSX SpoofGuard, VMware NSX keeps track of ARP addresses to IP addresses and if these change. This way, if there is an unexpected change of IP address to ARP address, the system can be blocked automatically. VMware NSX SpoofGuard allows for the creation of specific networks and gives administrators the ability to allow certain IP addresses. SpoofGuard monitors by means of a couple of mode settings:
- Automatically trust IP assignments on their first use (TOFU) – This mode trusts the first IP address reported to the NSX Manager.
- Manually inspect and approve all IP assignment before use – This presents the set of IP addresses discovered for approval by users. This mode blocks all traffic by default.
With DHCP environments the “trust on first use” is not recommended as IP addresses are dynamic and will be changing in a dynamic fashion. This does not lend itself to the TOFU, since it would only trust the first IP address used by the virtual machine.
Configuring VMware NSX SpoofGuard
The configuration of VMware NSX SpoofGuard is very simple and is only a few clicks worth of configuration to enable it. Under Networking & Security >> SpoofGuard we are able to see and configure the settings of SpoofGuard. By default, it is disabled. If we click the Change button below, we are able to change the Global IP Detection Type.
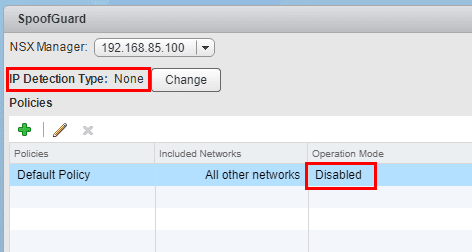
In the Change Global IP Detection Type dialog box, we select ARP Snooping.
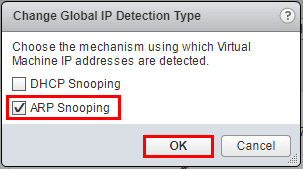
Now, we see ARP listed in the detection type. Click Default Policy and then click the “Pencil” icon to edit SpoofGuard.
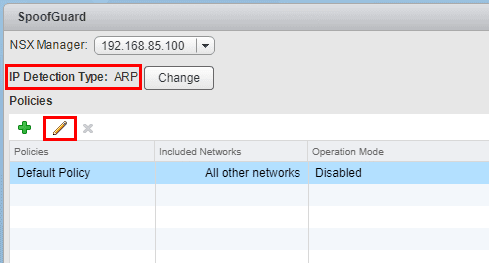
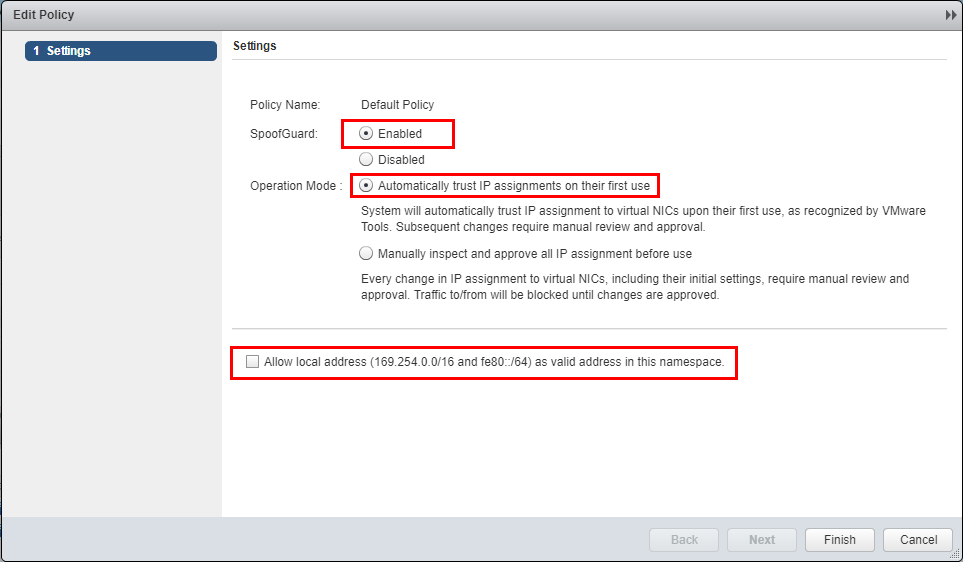
Here we enable SpoofGuard. To do that, you simply change the radio button to Enabled and select the Operation Mode. In DHCP environments, TOFU is generally not the recommended mechanism since IP addresses will change from time to time. The manual means of allowing IP addresses will most likely be automated in large dynamic environments.
Also, note the checkbox at the bottom to allow local addresses. Virtual machines will at first configure a link local IP address in the form of 169.254.0.0/16 or IPv6 address of fe80::/64. This setting allows these to be included in the allowed IP addresses.
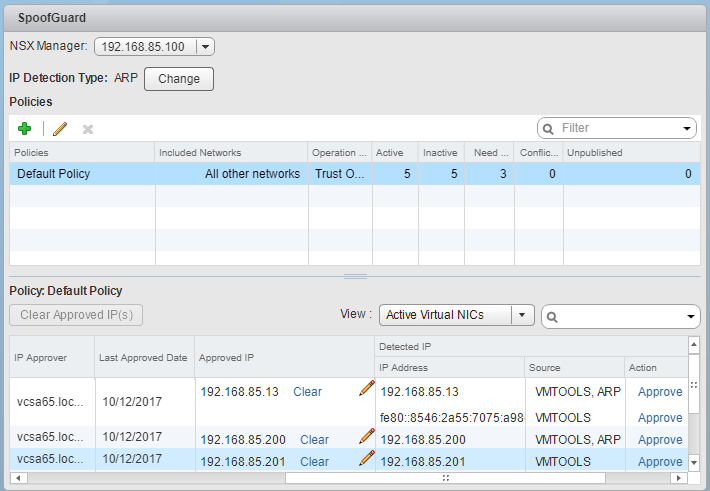
Below, we see the default policy enabled and we already see our active IP addresses showing up in the table. They will come across as automatically approved.

Thoughts
If you are new to VMware NSX and wondering What is VMware NSX SpoofGuard, hopefully this high level overview will help with a general understanding of the purpose of this functionality in NSX as well as the quick and easy way to get it enabled and running. ARP spoofing is a tried and true method attackers often use to gain access to production systems while on a network. VMware NSX SpoofGuard creates a security mechanism to establish a trust between an ARP address and IP address based on chosen metrics and then applying policy when that relationship is broken.