Enhance Security with Backup Technology
Malware infections and particularly Ransomware, can account for some of the costliest disaster recovery scenarios that your enterprise environment today may face. When it comes to backup software, many organizations are considering backup software purchases as an investment in security (not just business process integrity and continuity). Ransomware is becoming increasingly sophisticated due to the persistence of hackers and data thieves alike. So, the number of IT security breaches is growing at an alarming rate. Let’s examine how we can use backup technology to solve many of the concerns and issues surrounding Ransomware and data loss prevention and remediation. Also, let’s see how we can enhance security with backup technology.
Backup Technologies that ensure minimal downtime
When we take a look at a modern backup solution like Nakivo Backup & Replication, Nakivo offers several key technologies that ensure minimal downtime when you are affected by Ransomware – VM Replication, Backup Copy, Flash VM Boot, Instant File recovery, and Full VM recovery. When critical business systems are down, Recovery Time Objective or RTO becomes crucially important. Let’s take a look at the features mentioned above in detail and see how each can be powerful tools when recovering from data loss caused by a Ransomware infection.
VM Replication
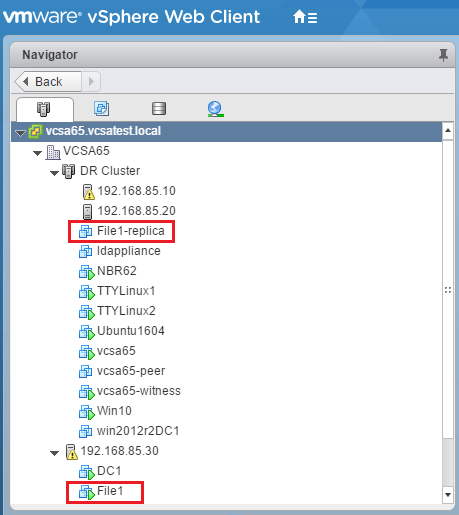
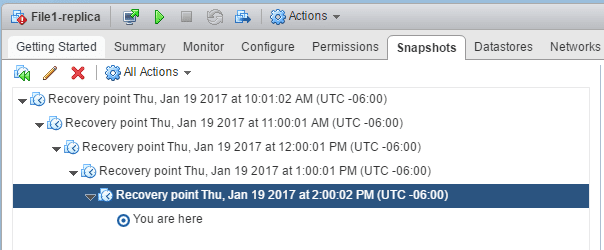
The Nakivo VMware vSphere Replication job essentially creates a “hot standby” replica VM that is powered off in a secondary virtualization environment, typically at a DR location that can be powered on in the event the primary VM is offline. Why is this important? If, in the case of Ransomware, the primary server resource in the production environment is damaged, the replicated copy of the VM could then be powered on in the DR location and service can be restored very quickly. As you can see below, using the VMware vSphere Replication job, we have created a replica VM in our “DR Cluster” environment. You can also choose to keep a number of recovery points which means you have certain points in time you can restore to with the VM replica if need be.
The replicated VM keeps the specified number of recovery points for additional granularity in replicated VM restore point provisioning options.
Backup Copy
The backup copy job is an integral component to the security of mission critical data. Backup copy jobs copy the backed-up data to another location. It is imperative that any modern backup solution today has the functionality of being able to create a secondary copy of the backup data. In the event that due to a Ransomware infection the backed-up data in the primary backup repository is corrupted, then with the backup copy, you have another copy of the backup data in a separate location/repository.
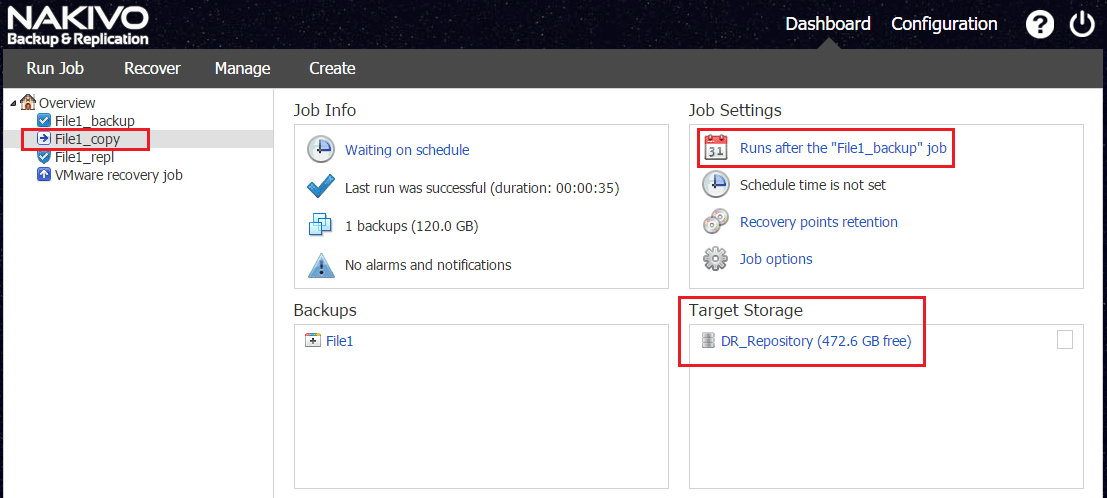
As you can see below, we are scheduling the backup copy job to run after the production backup, so as soon as a production backup finishes to the primary repository, we will have the most recent backup copied to our secondary location. Notice the target storage in this example is our repository in DR.
If our primary Nakivo backup server was compromised due to Ransomware infection, we have the backup copy repository available for use as an alternate restore source.
Flash VM Boot
Aside from a replicated copy, the flash VM boot is perhaps the quickest way to get a VM back up and running. With Flash VM boot, the entire VM is booted directly from the compressed and deduplicated VM backup. So, if a server is corrupted, won’t boot, or is otherwise unable to carry out a business-critical function, using the Flash VM Boot feature can have your server back up and running in literally minutes. The Flash VM boot technology provisions iSCSI connections to present VM disks stored in the backup repository directly to an ESXi host. This saves the time of having to restore the VM to the local ESXi datastore and then booting the VM. Instead, the VM is running from the backup files themselves.
When the VM is created, Nakivo Backup & Replication creates a snapshot of the VM. All changes that occur to the VM are then stored in the snapshot.
Instant File Recovery
What if in the case the entire server is not corrupted (operating system and configuration is unaffected and intact) – only specific files were encrypted by Ransomware and rendered unusable? We can then use the Instant File Recovery to retrieve the specific files that need to be restored, and restore them.
Let’s think about a potential scenario. Users in accounting have some important documents that have been infected by Ransomware and rendered useless.
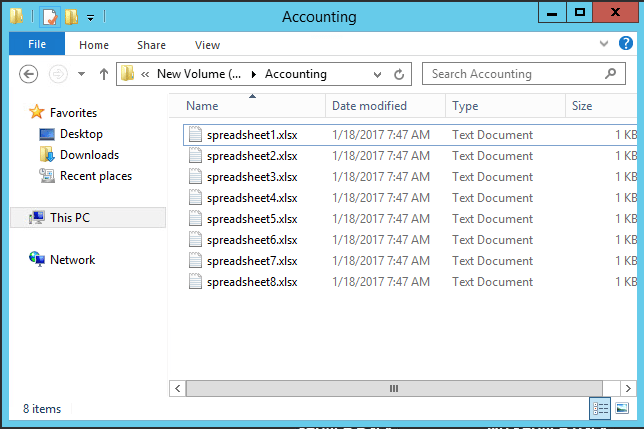
Our server before:
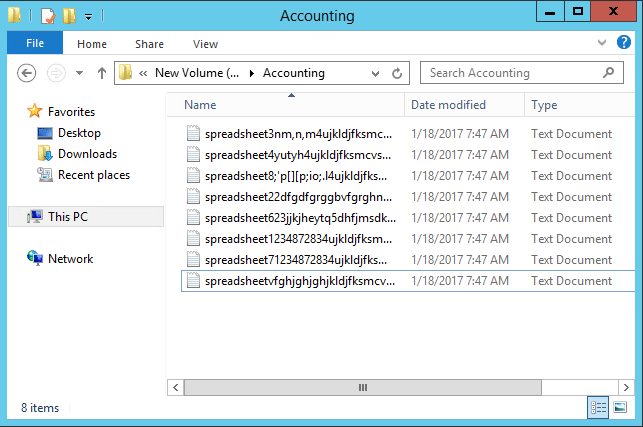
After Malware infection – file names contain random letters and are encrypted.
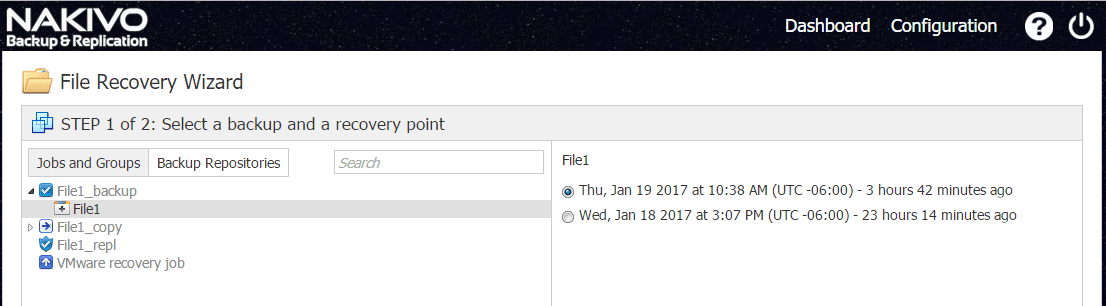
To restore using the Instant File Recovery, we first pick the restore point we want to restore from.
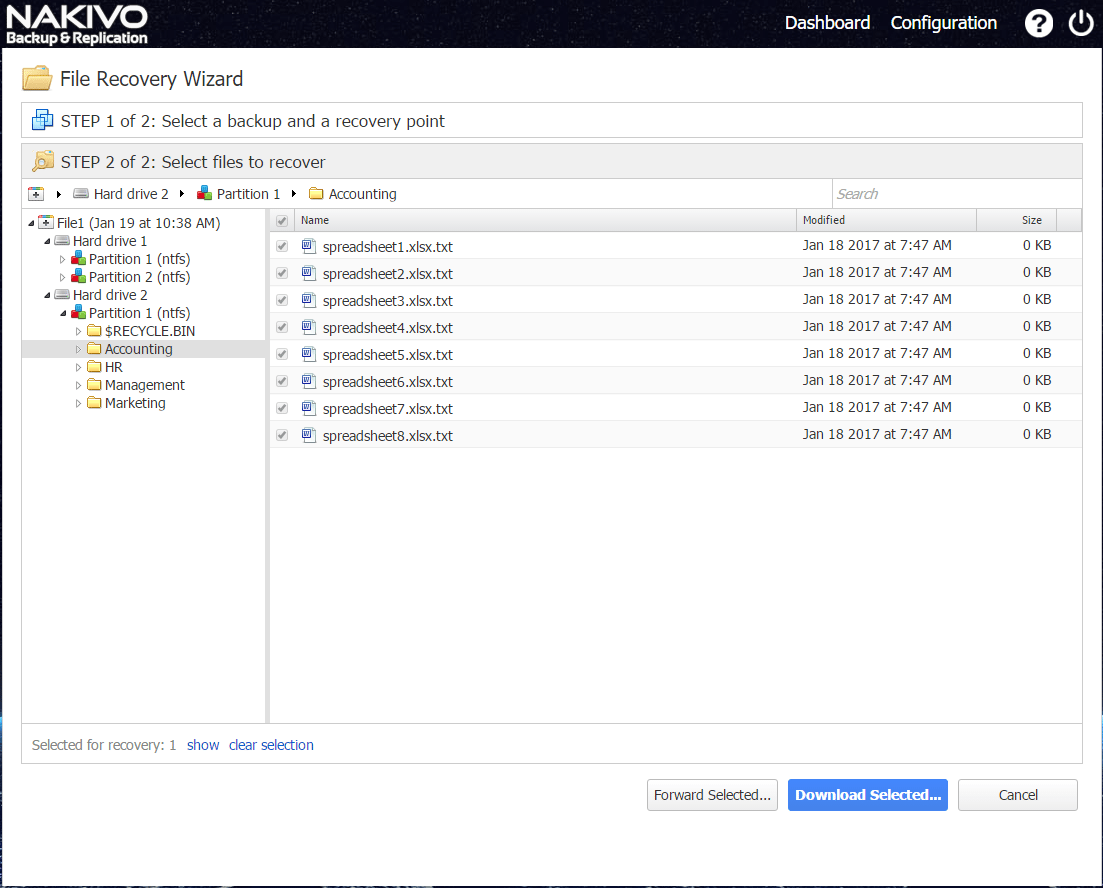
Then, we select the files we select the files we want to recover and Download them or even email if we choose. These files can then be copied over to the server in an alternate location or in place of the corrupted files.
Full VM Recovery
Full VM Recovery is essential when thinking about being able to recover from a Ransomware attack. Being able to completely reconstruct a virtual machine from the operating system, configuration, as well as end user files is crucial to business continuity. With this option, we are choosing to fully restore the VM from the Nakivo backup repository. The Full VM Recovery option can have up to 1000 recovery points and can choose any one of those for a Full VM recovery. We can restore to the original location or to a new location which can be local or offsite.
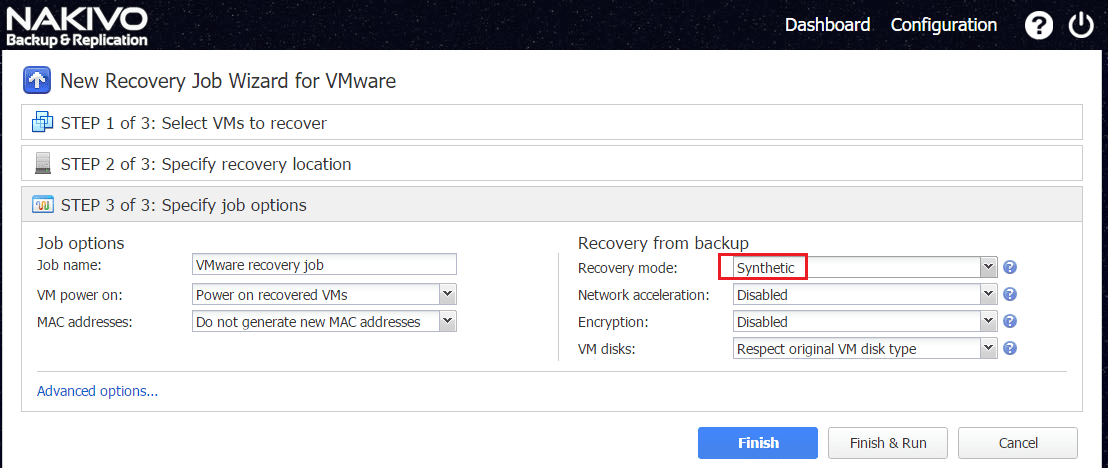
If the integrity of the production site has been compromised by Ransomware and other VMs have been affected as well, we may choose to restore the VM offsite in a clean DR environment. The nice thing about the Full VM Recovery with Nakivo is that it is a full synthetic operation that removes any dependencies on the original environment to bring the VM back online. The last thing you want is to have dependencies on the original site or equipment during a DR scenario caused by Ransomware or other cause.
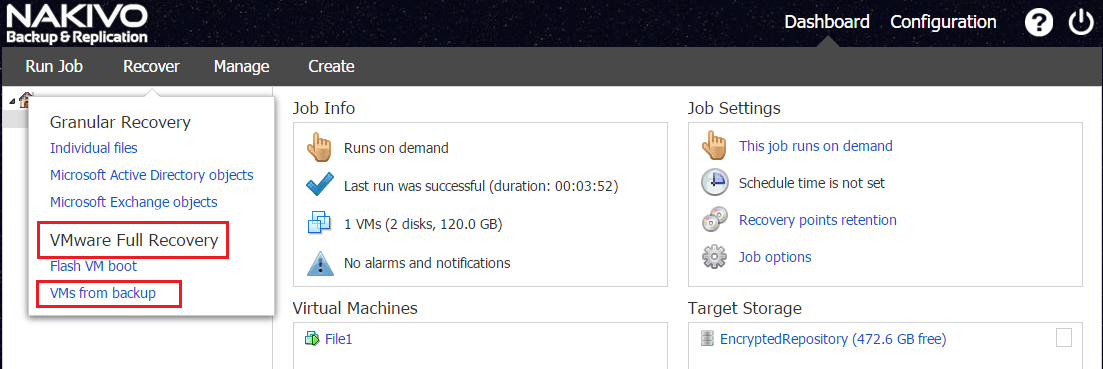
Below we are selecting to Recover using the VMware Full Recovery option with VMs from backup.
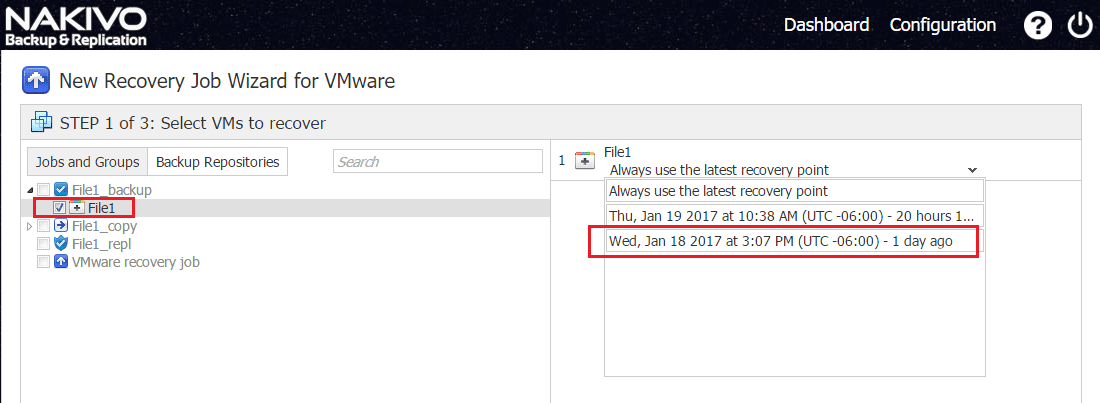
Next, as mentioned, we can select a point in time to restore from.
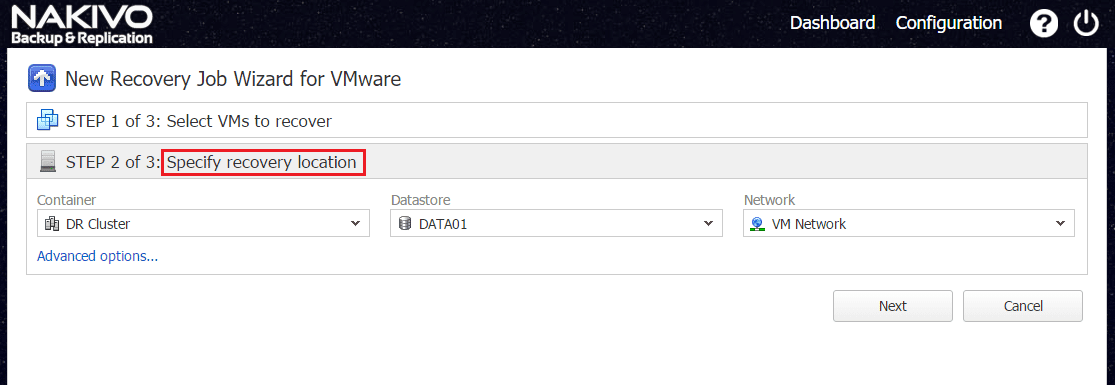
We select the location. Here we have selected a DR location for recovery.
Finally, we select the restore options.
Thoughts
In today’s world of constant security threats coming from many different sources, backup solutions are no longer simply data recovery mechanisms, but are also part of the overall security plan of an organization. We can Enhance Security with Backup Technology. With serious threats to business continuity such as Ransomware that can render a business crippled in a matter of hours or even minutes, you need a backup solution that can meet the challenge of recovery time objectives (RTOs) in the minutes and not hours. Nakivo Backup & Replication is a great example of a backup solution that can cover all angles of recovery due to malware or other disaster recovery scenarios.