Recently, Microsoft released the official support version of Enhanced Mitigation and Experience Tookit or EMET version 5.5. Per Microsoft:
“The Enhanced Mitigation Experience Toolkit (EMET) helps raise the bar against attackers gaining access to computer systems. EMET anticipates the most common actions and techniques adversaries might use in compromising a computer, and helps protect by diverting, terminating, blocking, and invalidating those actions and techniques. EMET helps protect your computer systems even before new and undiscovered threats are formally addressed by security updates and antimalware software. EMET benefits enterprises and all computer users by helping to protect against security threats and breaches that can disrupt businesses and daily lives.”
With Version 5.5 there are a number of improvements and notables:
EMET 5.5 release includes new functionality and updates, including:
- Windows 10 compatibility
- Improved configuration of various mitigations via GPO
- Improved writing of the mitigations to the registry, making it easier to leverage existing tools to manage EMET mitigations via GPO
- EAF/EAF+ perf improvements
- Untrusted font mitigation for Windows 10
For us administrators in the enterprise, EMET is yet another layer in the security onion that can help protect end user systems. EMET can help to protect against zero day exploits and other security related threats that come the way of the browser, email, and other 3rd party applications. And with the new features for GPO configuration this makes this release an even more attractive offering for the enterprise. The great thing about EMET is that it is a free download from Microsoft.
Download EMET from Microsoft: https://www.microsoft.com/en-us/download/details.aspx?id=50766
Let’s take a look at how to install and configure EMET 5.5 in Windows 10.
Installation
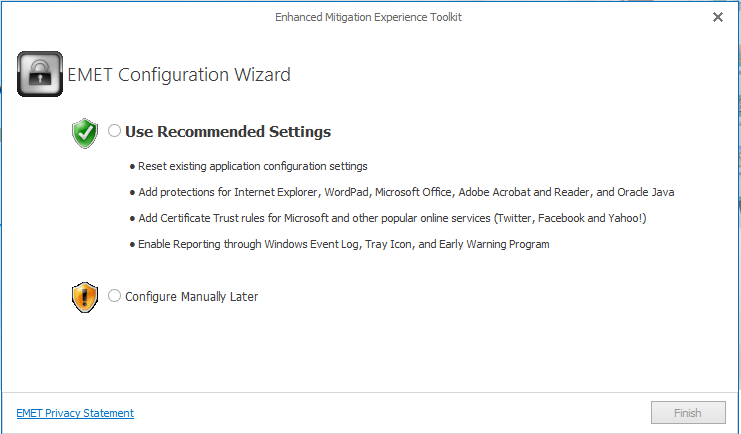
During the install, you will be prompted with the EMET Configuration Wizard, which presents the two options to Use Recommended Settings or Configure Manually later.
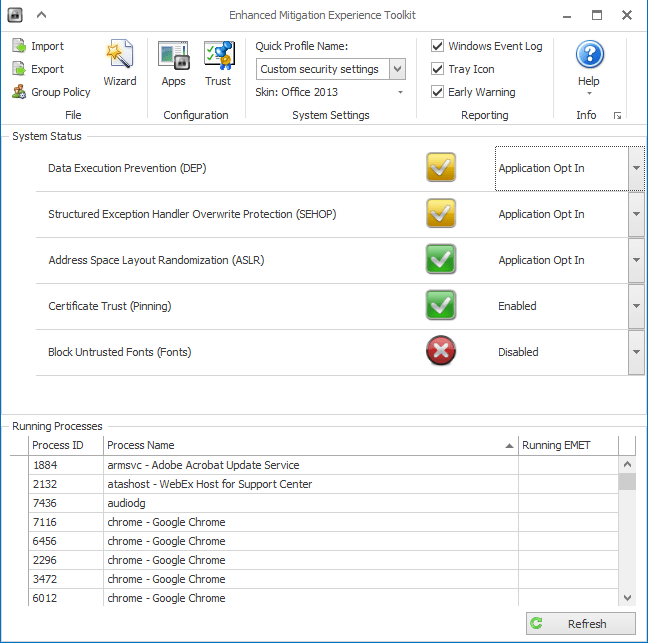
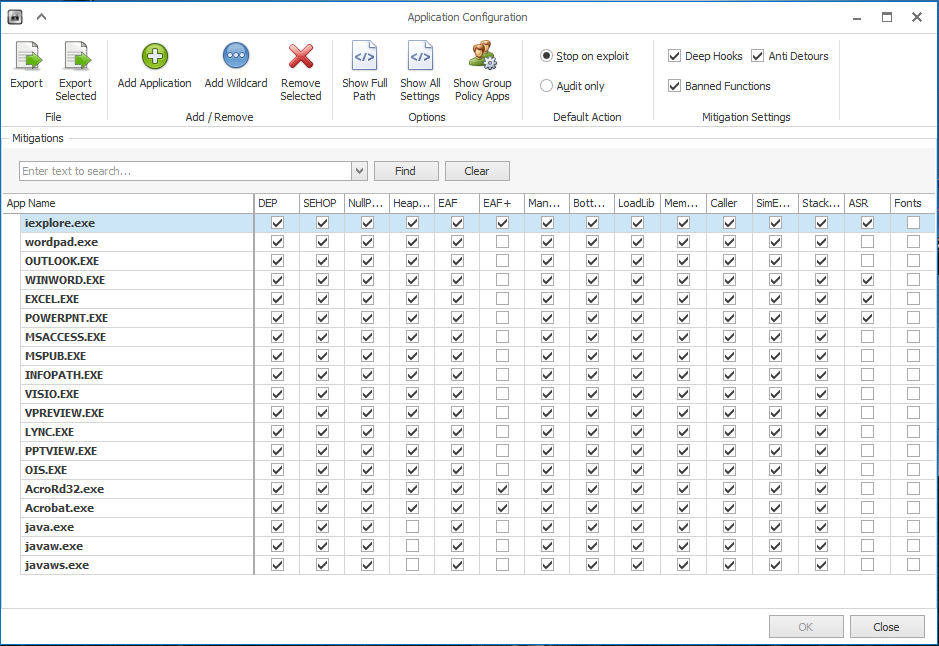
Below are a few of the options you see when launching EMET 5.5. Below are a few of the configurable parameters – Data Execution Prevention (DEP), Structured Exception Handler Overwrite Protection (SEHOP), Address Layout Randomization (ASLR), Certificate Trust (Pinning), Block Untrusted Fonts (Fonts).
Also there are a myriad of configurables for applications installed in a pretty intuitive checkbox format allowing you to quickly check or uncheck options for certain applications.
Final Thoughts
Having used EMET through a few iterations now, it is becoming a more solid and viable product to bolster security in Microsoft operating systems. It is definitely a worthy addition to virus protection as it helps to round out attack vector security.