So many times, the discussion comes up with using vlans , how to use them, and when they need to be implemented, especially in best practices using vlans with iscsci and vmotion. Do you always use vlans with iscsi and vmotion or is it a case by case basis?
Let me say this – you will not go wrong using vlans in a VMware environment to segregate iscsi and vmotion traffic on every install in my opinion. However, there are some factors that can be considered to decide whether or not vlans are better to use than not in a case by case basis.
How much bandwidth and link speed?
If you are using on gigabit capable switches, it is ALWAYS best practice to employ vlans to segregate your different networks. With gig connections you are already dealing with a more limited amount of bandwidth. To ensure you have dedicated network traffic space, use vlans to ensure you don’t have bandwidth issues for your iscsi connections, vMotion, etc.
On the other hand, if you are using 10 gig switches with multiple connections for iSCSI and vMotion, vlans are not as important, because the backbone for carrying your data is much larger and especially if you don’t have competing traffic other than iscsi and vMotion on the switch, you probably won’t see any performance difference.
How many different types of traffic?
Do to budget reasons or other environmental factors some use their iscsi switches for more than just iscsi, vmotion and other types of traffic. They may be using the switch stack to aggregate other types of traffic.
If you have many different types of traffic and networks aggregated in the same switch, vlans are definitely something you want to deploy on your switches to segregate traffic and to help enforce dedicated network boundaries between your traffic spaces.
Management Interface
Another more minor reason to consider whether or not to employ vlans on your storage switches is whether or not they have dedicated management interfaces. If your switch has a dedicated OOB management interface, you can address this interface for remote management or management on your LAN. This traffic is not switched traffic through the rest of the switch fabric.
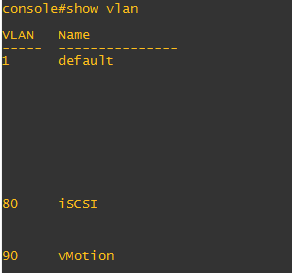
However, if your switch does not have a dedicated management interface, most likely you will be assigning an IP on vlan 1 which is the default vlan for most all switch manufacturers so on a flat switch (no vlans) any uplinks to the switch would be “connected” to the rest of your management network. Also, other uplinks would also try and grab DHCP addresses when connected to the switch if not otherwise assigned which in most environments is not desirable.
Recently, case in point, I was working with a pair of Dell N2024 switches which have no dedicated management interface. So in addition to other reasons mentioned above, I carved out two additional vlans for iSCSI and vMotion to segregate these networks from the management network of vlan 1.
Final Thoughts
As with any answer there are always exceptions and different ways of doing things based on the needs of a specific environment. So there is no “cookie cutter” answer that perfectly fits every scenario. Vlans are like any other tool – they have their place and can be properly used and then also misapplied. Please share your thoughts or input in your specific experiences using vlans with iSCSI and vMotion.
Google is updating how articles are shown. Don’t miss our leading home lab and tech content, written by humans, by setting Virtualization Howto as a preferred source.