Sophos UTM Block web traffic for only one host
Within Sophos UTM, as much as I like the product and have enjoyed using it in my home lab environment, blocking a single host from being able to hit the web is really not very intuitive at all. In other products, you normally are able to restrict a client from a certain traffic zone or add them to some sort of black list firewall rule. However, in Sophos UTM, the way the appliance processes rules makes for this simple process being more convoluted that one might imagine.
Sophos UTM processes rules in the following DNATs, Proxies, Packet Filters and Static Routes, SNATs, before the firewall rules are processed. With this being the case, the web filter if turned on will pass traffic if it matches the filter profile already in place regardless of whether or not the firewall rule is explicitly blocking. This order of precedence is not one that I am particularly fond of as you would imagine that firewall rules would be the gold standard for all traffic that is coming through the pipe when it enters and exits the UTM. However, understanding is more than half the battle so with this information we can see how to correctly block web traffic.
Sophos UTM has a mechanism for using web filter profiles that we can leverage to match traffic from a certain network or host to be able to accomplish what we are trying to do.
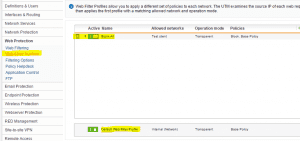
Navigate to Web Protection >> Web Filter Profiles and then add a new web filter profile. Below I have added a new one and named it Block All.
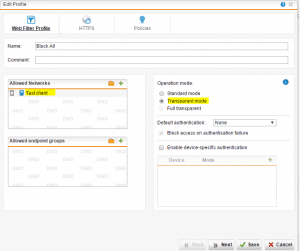
Below when we drill into the settings, you can specify the Allowed Networks which essentially is the network or host that you want to disallow access in this case. We leave transparent mode selected as we don’t want to have to configure a proxy on the client side.
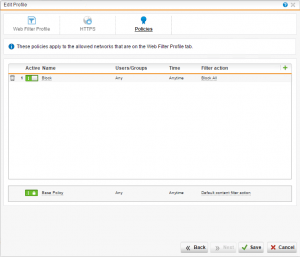
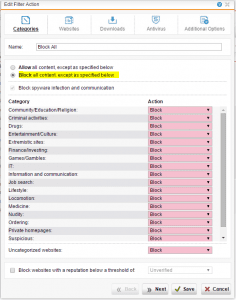
On the policy tab we create a policy that has a name of Block with the filter action of Block All.
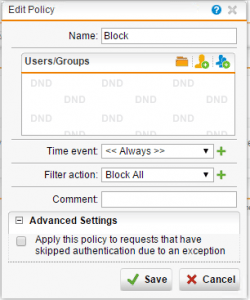
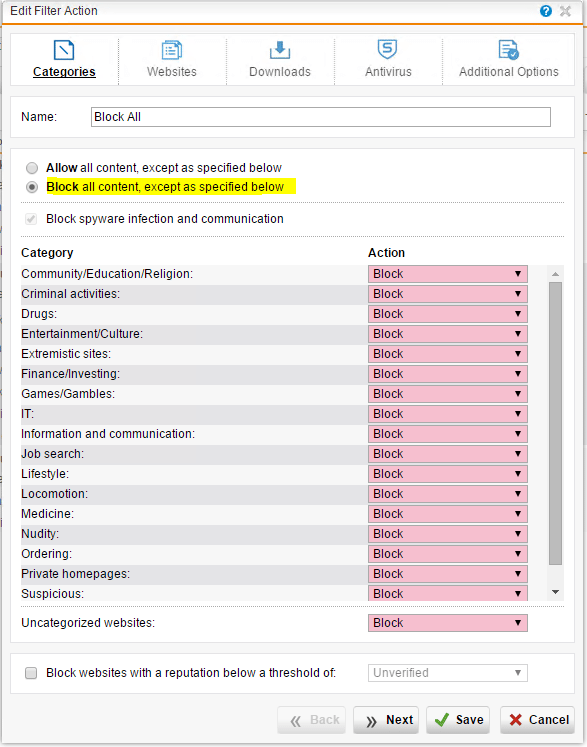
A closer look at the Block All filter action that we created shows that we “Block all content, except as specified below” and then have the Action set to Block for every category.
This very specific web filter profile will match our client before it hits the default web filter profile which will catch all the other web filter traffic. This allows us to block all web traffic to the specific host in question without any firewall rules!