A really cool fun project I have been wanting to take on at home for a while now is to create a DMZ environment using my Cisco SG300-20 switch, VLANs, inter vlan routing, ACLs, and VGT or VST. If you have a fully featured switch such as the SG300-20 you can do a lot of cool routing of traffic and segmentation all within the switch itself. In essence, you can create a “poor man’s” DMZ in a sense.
Scope of the Project
- Create a separate VLAN for DMZ (forward facing traffic)
- Create a separate subnet for DMZ related traffic
- Use inter vlan routing on the switch to take care of traffic routed to your firewall
- Secure traffic between your DMZ network and your “management” network using ACLs present on the switch
At home I am running a Cisco SG300-20 switch which is fully capable of layer 3 routing which you want to be able to do inter vlan routing, however, even if you don’t have a switch that can perform layer 3 functions, as long as it can do layer 2 VLANs or 802.1Q. The reason for this is that you can also not do inter vlan routing and use your firewall to route traffic using a subinterface in most cases but each vendor will be different on setting up your configuration, so be sure and check with your particular firewall or UTM manufacturer.
For the purposes of this post however, we will be using inter vlan routing to accomplish our routing between VLANs as well as securing access to each VLAN from other VLANs. Typically in a small environment you won’t see much of a gain from using inter vlan routing on a layer 3 switch, however, in a large production environment, a firewall or router even is not designed to do the fast routing and switching between vlans as efficiently as a layer 3 switch, so the best practice in an environment with a lot of traffic and VLANs is to use inter vlan routing.
Create the DMZ VLAN
The process of actually creating the VLAN for the DMZ is simple. I will use the SG300-20 switch in this example. So to setup a VLAN, simply issue the command:
switch#(config)vlan 50 - where 50 is the VLAN number you want to designate for the DMZ
The above will actually create the VLAN. Simple right? Nothing to it basically.
You will then most likely want to name the VLAN something intuitive like DMZ for instance.
switch#(config)int vlan 50 switch#config-if)name DMZ
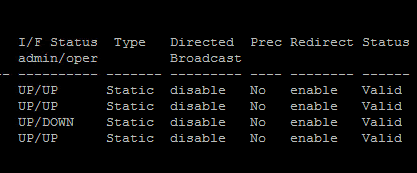
Now the heart of inter vlan routing is setting up SVI’s (Switch Virtual Interface) on our VLAN interfaces which are used to do the routing of traffic. Actually when you set a management IP address on your layer 3 switch, you are basically setting up your first SVI on the switch. The virtual interfaces are used as routes for clients that sit on those particular VLANs.
switch#(config-if)ip address 192.168.50.1 255.255.255.0
So above, we are in the interface configuration for VLAN 50 and we then set the IP address that will be used for the SVI on VLAN 50.
Setup Inter VLAN routing
At some point along the way most layer 3 switches need to be told they are layer 3 devices as most only default to having layer 2 capabilities. On most enterprise Cisco switches, you can simply issue the command at the global configuration prompt:
switch#(config)ip routing
The SG300-20 is a little more involved in setting up layer 3 but nothing difficult. See the post here about setting up VLANs in general and how to turn it into a layer 3 switch. After you have turned on the layer 3 features of your switch, we can now do some cool inter vlan routing between VLANs and subnets.
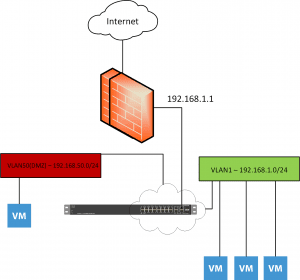
The SVI that exists on the same network as the upstream firewall or router, will be the SVI used to route traffic back to all the other VLANs internal to the switch. So, if on VLAN 1 I have an address of 192.168.1.2, VLAN 20 – 192.168.20.1, VLAN 30 – 192.168.30.1 and the upstream firewall is 192.168.1.1, the 192.168.1.2 interface will be the route we will add on the firewall to get back to the other VLANs as well. So 192.168.30.X/24 route on the firewall will point back to 192.168.1.2 on the switch for its next hop.
Also, on the switch, you would set the default gateway of the switch to your upstream firewall/router. For instance on the SG300-20:
switch#(config)ip default-gateway 192.168.1.1
This will give allow the switch to route all traffic from the VLANs out to the default gateway address. The firewall/router’s route back to the switch SVI will allow the traffic to get back to the particular VLAN.
Setup ACLs to prevent traffic from crossing VLANs
The last step we have in securing our DMZ VLAN is to put an ACL in place to prevent traffic to and from the DMZ VLAN except for traffic we want to come across. In the below, we create the access-list giving it a name. The next line permits traffic from the VLAN to the upstream firewall/router address. The line after that denies any other traffic from 192.168.50.X to 192.168.1.0 network which will deny everything else besides traffic destined to and from our upstream router. The last line will then permit any other traffic that doesn’t match what we have defined in the lines above it.
So basically we have prevented traffic to our management VLAN and then allowed all other traffic from the DMZ VLAN in and out to the upstream firewall/router.
ip access-list extended DenyVLAN permit ip 192.168.50.0 0.0.0.255 192.168.1.1 0.0.0.0 deny ip 192.168.50.0 0.0.0.255 192.168.1.0 0.0.0.255 permit ip any any
Conceptual Drawing of the Setup
Final Thoughts
Inter vlan routing is a really great tool to use in your home lab or in production to quickly and efficiently route traffic between VLANs. In a lab scenario you can effectively create a DMZ VLAN using inter vlan routing, ACLs and a firewall of your choice. More to come on home lab networking projects! Stay tuned…








Awesome post, thanks!! it was most helpful