How to connect Shrew Soft VPN client to Sophos IPsec VPN
So far I have really been impressed with the features and power of the Sophos UTM appliance. I have ran it both in a software based applianced running on a whitebox atom powered machine and also in a VMware virtual machine which is the current configuration I have running due to the great CPU power I have available from my VMware host. The Sophos UTM appliance provides a very wide range of remote access options to access your network from a remote location. The options that exist are SSL, PPTP, L2TP over IPsec, IPsec, HTML5 VPN Portal, and Cisco VPN Client.
I want to cover the topic of setting up an IPsec VPN on the Sophos side as well as connecting to your Sophos IPsec VPN using the free Shrew Soft VPN client. Sophos offers a VPN client that can easily connect up to your Sophos UTM box by importing an .ini file from the UTM itself. I have tried this process and it is extremely easy and takes care of all the heavy lifting of getting the configuration right, however, the client is downloaded with a 30 day trial license. The client is quite expensive, especially if you are just purchasing a single seat of the software.
Unfortunately, there is no way to import the downloadable .ini file from the UTM into the Shrew Soft VPN client. However, as you will see below, you can connect to your IPsec VPN by manually configuring the client to connect to your Sophos UTM.
Sophos Setup
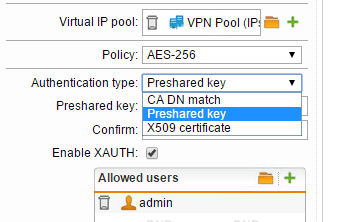
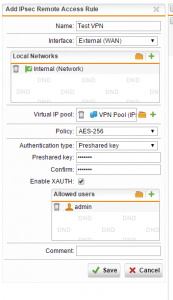
First things first, go down to the Remote Access link on the left side of the dashboard. Click IPsec and then click New IPsec Remote Access Rule… after which you will be brought to the screen to setup the VPN connection. Below I have named the VPN connection, set the Interface that the connection would listen on (External WAN), setup the Virtual IP Pool which is set by default to the VPN Pool out of the box. You can choose between a number of policy profiles that you want to enable. I have chosen to setup a Preshared key Authentication type. Also, you can enable XAUTH which will increase security by also requiring a username and password for that user.
The user is specified underneath the Allowed users box that appears after you select Enable XAUTH. Once you setup the user, simply hit Save.
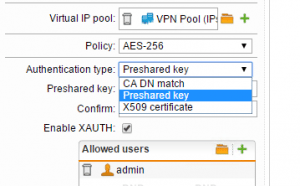
Below is a quick capture of the Authentication type dropdown where you see you can select between CA DN match, Preshared key, and X509 certificate.
Be sure after you click Save on the Access Rule screen, that you enable the VPN by sliding the slider next to the VPN connection over to green, which effectively enables the connection.
Shrew Soft
After you have created a VPN connection on the Sophos side using the settings we mentioned above, you can now begin to setup your Shrew Soft connection via the free Shrew Soft VPN client download which can be found here. The installer is very small in size and installs in a snap.
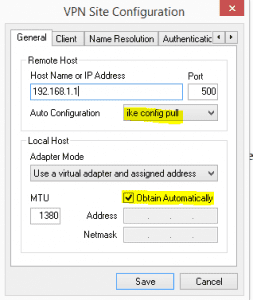
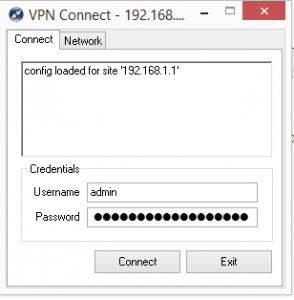
After installing Shrew Soft, simply create a new connection. Enter your public WAN interface address that you setup on the Sophos side. Note below, I have a 192.168.1.1 address showing just for purposes of documenting the setup.
- Make sure under the auto configuration section to select ike config pull and then under the Adapter Mode to select obtain automatically
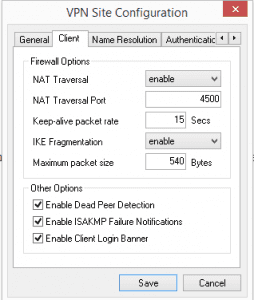
Leave the default settings under the NAT traversal options
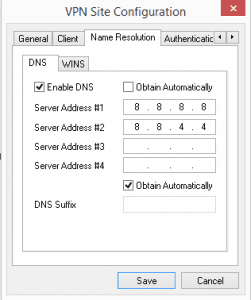
Under name resolution in my particular config, I setup public DNS resolvers, however, these can be set to any that you wish, or selected to Obtain Automatically which should pull from your Sophos VPN addresses DNS configuration.
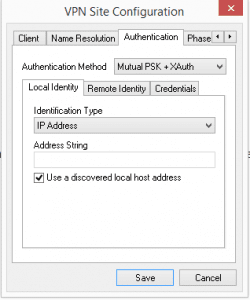
Since I am using a preshared key and XAUTH, I have selected that below under the Authentication tab. Also, leave the Identification type under Local Identity as the default IP Address.
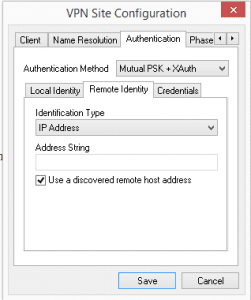
Still in the Authentication tab, leave the default Identification Type for Remote Identity selected as IP Address.
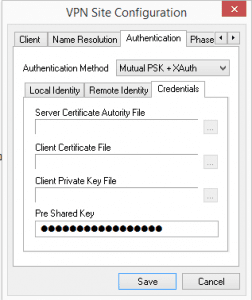
Under the Credentials tab you will need to specify your Pre Shared Key
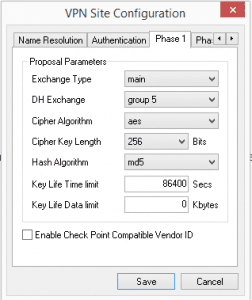
The settings below were matched up to the AES 256 policy I am using for the Policy type on the VPN connection on Phase 1.
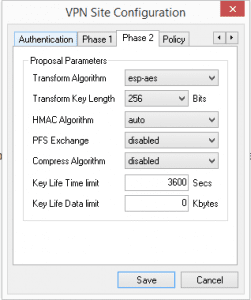
Same goes for Phase 2.
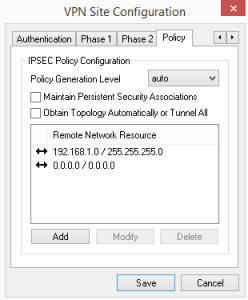
Under the Policy tab, you specify Remote Network Resource. I have the local LAN subnet specified as well as the 0.0.0.0 network which allows the machine to browse Internet resources as well.
After you finish the Policy tab, you should be ready to go to test the VPN connection. Save the connection above and then double click it and you should see a screen similar to the below where you will be asked for your XAUTH username and password that you specified on the Sophos UTM side.
Final Thoughts
I am really liking the remote access capabilities of the Sophos UTM. There is a wide range of builtin options that will cover just about any need that you would have to establish a remote VPN connection to your Sophos UTM. Shrew Soft is an awesome VPN with a lot of capabilities that will allow you to connect to just about any type of VPN connection that you need to connect up with. Hopefully the tutorial above will help those of you out there who are looking for a free client that can connect up with the Sophos UTM without having to spend the money on the Sophos VPN client. The genuine Sophos client is a great client and works rock solid as it is basically NCP client that has been rebranded. However, the price of the client can be a slight sticker shock.
If you are looking for a free way to achieve the same results, you can’t go wrong with the Shrew Soft client as it works perfectly in connecting to the IPsec VPN of the Sophos UTM.











I know You wrote this a while back, but it was a great guide to get me up and going. My in-house programs are working very well outside, but one issue I am having is DNS and resolving web pages. I have tried using the Google DNS, Internal DNS, and the sophos as DNS and cannot resolve web pages. I can ping them by name and get good stats, but timeouts trying to resolve them in a browser. Would you have any ideas?
Jerry,
Under Network Services >> DNS make sure you have allowed your DMZ Network to use Sophos as a recursive DNS resolver. From what you describe is sounds like Sophos is blocking your DNS queries from your connected DMZ client.
I had tried this, still to no avail. Not sure what the problem is. Thanks for the help. For that user a few months back we just went another route, but I am at it again trying to make the vpn work.
I had tried this, still to no avail. Not sure what the problem is. Thanks for the help. For that user a few months back we just went another route, but I am at it again trying to make the vpn work.
Jerry, have you taken a look at the Live log on your firewall? You may discover that you still have traffic being blocked. I did look at my firewall rules and I see that I have a listing for sources: myvpnuser (User Network), Services: Any, Destinations: Internal (Network) and Internet IPv4….most likely you still have some traffic being blocked somewhere. The live log is the best place to start. Connect as your user to VPN and try to browse some web pages and the firewall log should alert you to anything being blocked….best, Brandon
Brandon, Thanks for all of the help. I am going to start from scratch and give it another go. I had that rule as well. $usernetwork.>>any>>internalnetwork [allow].
Other question. What kind of transfer speeds are you seeing with this solution? The reason we took the first user another direction is that the CRM he uses would hang and crash over the VPN. I figured it was size of db files being called on. The connection (tried from multiple locations) seemed very laggy.
Jerry,
Sounds great, hopefully you can get to the bottom the Internet issue, let me know…..on speeds, I seem to get pretty decent VPN speeds, however, I am connecting to a rather lightweight whitebox with 4GB of RAM and nothing really exciting processor wise but a fairly large connection. Are you using a Sophos appliance? Also, what size is your connection? What encryption are you using?
I thought I may have found something by adding the vpn pools to the web filter as well, but still having some weird issue getting pages to resolve. Must have a setting mismatch somewhere….
We have a dedicated 20/20 fiber line. A Sophose 320 UTM with 4gb of ram. CPU sits at about 9% and ram at about 38% typically. At home I have a 50/5 connection from Charter, which I know won’t be the best for running this sort of set up. I tried running my set up exactly as you laid it out here with the adjustments for my environment.
Jerry, I just remembered also – did you by chance create a masquerading rule for your VPN user network? My rule is as follows: Network: vpnuser (User network), Interface: External (WAN), Use address <> ….If you don’t have the masquerading rule, you won’t be able to get out to the Internet.
Again Brandon, I really appreciate you taking the time to help. I do have the masquerading rule created. I cross-referenced your post with Sophos’ pdf guide for creating an IPSec connection. It seems like it should be something very simple, but I swear I have checked your guide and theirs about 20 times and I am not seeing anything, unless my particular environment has some quirky setting that is halting it. Maybe tonight I will take the time to watch all the logs as attempt to work and see what I get. I did however try running it with ATP, IPS and the web filter turned off and it made no difference.
No problem Jerry – It improves the knowledge of us all to share and collaborate on issues. Quick question also, in the VPN client, did you specify the name resolution public resolvers as I have listed above or are you using other name servers? In your firewall rules in the UTM are you allowing DNS traffic to “Any” or are you restricting this down to particular addresses?
Thanks for this content but it didnt works for me 🙁
192.168.192.0/24 is my local lan
10.242.4.0/24 is the vpn pool
192.168.178.0/24 is the remote local lan
2016:11:29-21:12:02 utm pluto[53339]: | peer client is 10.242.4.1
2016:11:29-21:12:02 utm pluto[53339]: | peer client protocol/port is 0/0
2016:11:29-21:12:02 utm pluto[53339]: | our client is subnet 0.0.0.0/0
2016:11:29-21:12:02 utm pluto[53339]: | our client protocol/port is 0/0
2016:11:29-21:12:02 utm pluto[53339]: | find_client_connection starting with D_REF_IpsRoaClientVpn_0
2016:11:29-21:12:02 utm pluto[53339]: | looking for 0.0.0.0/0:0/0 -> 10.242.4.1/32:0/0
2016:11:29-21:12:02 utm pluto[53339]: | concrete checking against sr#0 192.168.178.0/24 -> 10.242.4.1/32
2016:11:29-21:12:02 utm pluto[53339]: | fc_try trying D_REF_IpsRoaClientVpn_0:0.0.0.0/0:0/0 -> 10.242.4.1/32:0/0 vs D_REF_IpsRoaClientVpn_0:192.168.178.0/24:0/0 -> 10.242.4.1/32:0/0
2016:11:29-21:12:02 utm pluto[53339]: | fc_try concluding with none [0]
2016:11:29-21:12:02 utm pluto[53339]: | fc_try D_REF_IpsRoaClientVpn_0 gives none
2016:11:29-21:12:02 utm pluto[53339]: | checking hostpair 192.168.178.0/24 -> 10.242.4.1/32 is found
2016:11:29-21:12:02 utm pluto[53339]: | fc_try trying D_REF_IpsRoaClientVpn_0:0.0.0.0/0:0/0 -> 10.242.4.1/32:0/0 vs D_REF_IpsRoaClientVpn_0:192.168.178.0/24:0/0 -> 0.0.0.0/32:0/0
2016:11:29-21:12:02 utm pluto[53339]: | fc_try concluding with none [0]
2016:11:29-21:12:02 utm pluto[53339]: | concluding with d = none
2016:11:29-21:12:02 utm pluto[53339]: “D_REF_IpsRoaClientVpn_0″[4] 88.153.safe.safe:4500 #7: cannot respond to IPsec SA request because no connection is known for 0.0.0.0/0===87.138.safe.safe:4500[87.138.safe.safe]…88.153.safe.safe:4500[192.168.192.233]===10.242.4.1/32
2016:11:29-21:12:02 utm pluto[53339]: “D_REF_IpsRoaClientVpn_0″[4] 88.153.safe.safe:4500 #7: sending encrypted notification INVALID_ID_INFORMATION to 88.153.safe.safe:4500
Hy weby. I do have the same problem. Try this:
-) Go To Remote Access -> IPSec
-) Modify the IPSec rule
-) Under “Local Networks” add “Any IPv4”
-) Change the Pre Shared Key
-) Save
Under Shrew Soft Client, change the Pre Shared Key with the one you’ve typed right now in the Sophos configuration.
Try now, it should work.
Giacomo