How to use Untangle to help prevent Cryptolocker infections
Cryptolocker is probably one of the most malicious and feared malware infections in quite some time. Most malware infections are a nuisance at most and a good sweep by a spyware utility such as malwarebytes will clean up the infection and you are back in business. However, Cryptolocker is not such a variant. With destroying your data and making it next to impossible to recover your data without paying the ransom fee, this malware means business. There are a number of preventative measures that need to be taken to tighten up security in your network to help circumvent this malicious bug. Having some type of gateway antivirus or UTM device is always a good idea to sanitize traffice at the WAN level.
With that being said one of the main avenues that I have seen this bug get inside many networks is by email. Let’s face it, email is still probably the number one means of communication inside and out of today’s networks in the business community and no SPAM solution is 100% bullet proof at correctly identifying email as SPAM or malicious. I am a big fan of Untangle server even in the free form as a really good gateway UTM device which can greatly reduce a network’s attack surface.
However, Untangle like many others did not catch this bug when it first debuted. However, I want to publish a few rules that I have put in place at a few client networks using Untangle which may help you to keep not just Cryptolocker but many other malware variants outside of your network in dealing with email and web traffic.
Untangle uses the popular Linux SPAM utility called SpamAssassin. What I was determined to do however, in lieu of Cryptolocker was not just use SpamAssassin to identify SPAM emails, but rather to quarantine ANY email which either had attachments that I didn’t want, or contained links directly to dangerous file types. This is how I accomplished that.
While it is not recommended or support to manually modify your config file for SpamAssassin, this is the means that I used to create custom rules which can be used to quarantine messages fitting your specifications. The config file for SpamAssassin in Untangle is located at /etc/spamassassin/local.cf
Open your local.cf file and add the following rules to your config file:
loadplugin Mail::SpamAssassin::Plugin::MIMEHeader mimeheader ZIP_ATTACHED Content-Type =~ /zip/i describe ZIP_ATTACHED email contains a zip file attachment score ZIP_ATTACHED 7.5 mimeheader EXE_ATTACHED Content-Type =~ /exe/i describe EXE_ATTACHED email contains a zip file attachment score EXE_ATTACHED 7.5 uri DANGEROUS_URL /.(exe|zip|scr|pif|php|cmd|bat|vbs|wsh)$/i describe DANGEROUS_URL URL contains executable content score DANGEROUS_URL 7.5
The above text is self explanatory, however, the top lines tell SpamAssassin that you want it to assign a SPAM score of 7.5 to any emails that contain ZIP or EXE attachments. This of course will result in a quarantine. The “uri” rules tell SpamAssassin to look for emails that have any links to exe, zip, scr, pif, php, cmd, bat, vbs, wsh files. Of course any of these can be tweaked to your liking in any environment. So, what I have found is that using SPAM assassin to not really correctly identify SPAM which often times contains malware, but rather use it to identify all emails that have these types of attachments or contain links to the above types of URLS is much more beneficial.
Also, to keep in mind, the above of course still follows any exceptions that you have setup in your Email configuration so keep that in mind – also scan size limitations apply to the rules above as well.
Web
By utilizing the web filter even in its free form, we can restrict web traffic which most likely could be dangerous. We can restrict files such as .exe and .zip from being ran from the web. Keep in mind this may cause some legitimate files to be prevented from executing such as updates for legitimate software and such. Keeping an eye on the event log for the web filter will quickly help to identify these.
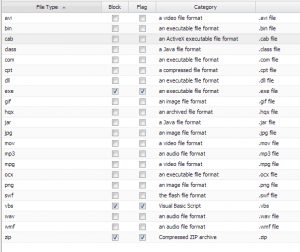
Under File Types for the Web Filter Lite you can block, flag, and even add file types. We have the .exe selected to block as well as .zip files which type we added.