How to find an infected network host sending SPAM messages
A very challenging situation in a network environment where you may have several or even hundreds of network hosts is finding a specific host that is infected with malware. Many variants of malware may send SPAM messages from the infected host resulting in warnings or violations from your ISP alerting you to the fact that you have a host inside your network sending SPAM. The problem is that these warning messages probably will contain the WAN IP or firewall address instead of the infected host as these days most networks are NAT’ed and use private IPs inside the network.
One of the best ways to find a host that is on your network sending SPAM out or any other malicious traffic is to use an Untangle UTM host/device between your internal network and firewall. Untangle is a great product even in its free version that can quickly identify malicious hosts or traffic on your network. Even if you don’t plan on using Untangle as a long term solution, it is easy enough to load up a host with Untangle, place it between your network and firewall, and identify the malicious traffic.
In our situation above, where we have a host that is sending out SPAM where maybe you have been alerted by your ISP, I want to show you how quickly you can identify a host sending out SPAM.
The Quick Process
The process below assumes that you have either loaded up an Untangle host or you are using an Untangle host that is already in place. If you don’t know how to cable the Untangle box, there are some really great tutorials here on the Untangle Wiki pages.
The first step is simply installing the available free rack module Spam Blocker Lite.
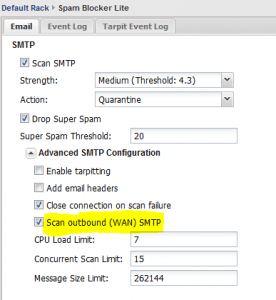
After we have loaded the SPAM blocker Lite rack module, we want t click on the Settings for this rack module and add a setting in the configuration. Note below, that you will need to expand the Advanced SMTP Configuration settings for the SPAM Blocker Lite module. Select the option to Scan outbound (WAN) SMTP. This will tell the module that you want to also examine outgoing port 25 messages for potential SPAM content.
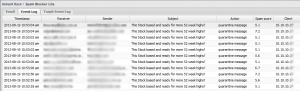
After you flag on the option to scan outbound (WAN) SMTP traffic, we can now take a look at the Event Log and see if we see a host that is sending mail. In the screenshot below, in our particular situation we saw a host IP that was filling up the quarantine logs with SPAM messages. We were pretty confident after seeing this host filling up the logs, that we had found the culprit.
We sorted the Event log listing above to include All SPAM events which will show only the SPAM emails and not the ones passed through. That quickly, we have identified the host that is responsible for sending out mass SPAM emails.
Final Thoughts
The Untangle product is a great UTM product for anyone especially who has no other hardware or software UTM in place and even for those who may already have something in place but who are not satisfied with the performance and results. The Untangle UTM makes finding rogue hosts as in the situation above in minutes instead of hours or days parsing through the network or sneakernet running virus scans or malware scans on all hosts just to find the one that is infected.